Free Microsoft MD-102 Practice Test Questions MCQs
Stop wondering if you're ready. Our Microsoft MD-102 practice test is designed to identify your exact knowledge gaps. Validate your skills with Endpoint Administrator questions that mirror the real exam's format and difficulty. Build a personalized study plan based on your free MD-102 exam questions mcqs performance, focusing your effort where it matters most.
Targeted practice like this helps candidates feel significantly more prepared for Endpoint Administrator exam day.
23190+ already prepared
Updated On : 3-Mar-2026319 Questions
Endpoint Administrator
4.9/5.0
Topic 1: Case Study Contoso, Ltd.Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and branch offices in Seattle and New York.
Contoso has a Microsoft 365 E5 subscription.
Network Environment
The network contains an on-premises Active domain named Contoso.com. The domain contains the servers shown in the following table.

You have a Microsoft 365 subscription that includes Microsoft Intune.
You plan to use Windows Autopilot to deploy Windows 11 devices.
You need to meet the following requirements during Autopilot provisioning:
• Display the app and profile configuration progress.
• Block users from using the devices until all apps and profiles are installed
What should you configure?
A. an app configuration policy
B. an app protection policy
C. an enrollment device platform restriction
D. an enrollment status page
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint.
You plan to onboard the following types of devices to Defender for Endpoint:
• macOS
• Linux Server
What should you use to onboard each device? To answer, drag the appropriate tools to the correct device types. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.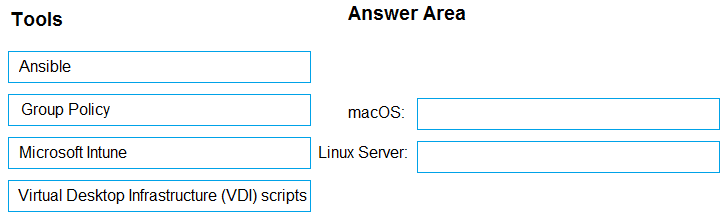
You have two computers named Computer1 and Computed that run Windows 10.
Computed has Remote Desktop enabled.
From Computer1, you connect to Computer2 by using Remote Desktop Connection.
You need to ensure that you can access the local drives on Computer1 from within the Remote Desktop session.
What should you do?
A. From Computer 2, configure the Remote Desktop settings.
B. From Windows Defender Firewall on Computer 1, allow Remote Desktop.
C. From Windows Defender Firewall on Computer 2, allow File and Printer Sharing.
D. From Computer1, configure the Remote Desktop Connection settings.
You have a Microsoft 365 E5 subscription that contains 100 iOS devices enrolled in
Microsoft Intune.
You need to ensure that notifications of iOS updates are deferred for 30 days after the
updates are released.
What should you create?
A. a device configuration profile based on the Device features template
B. a device configuration profile based on the Device restrictions template
C. an update policy for iOS/iPadOS
D. an iOS app provisioning profile
You have a Microsoft 365 subscription that contains the devices shown in the following
table.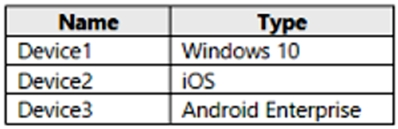
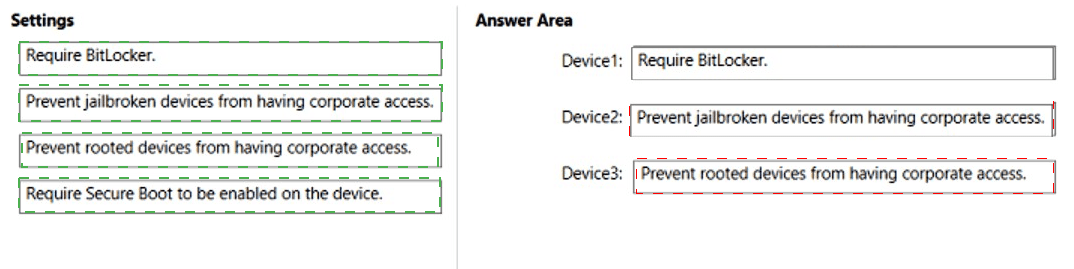
You need to ensure that only devices running trusted firmware or operating system builds can access network resources.
Which compliance policy setting should you configure for each device? To answer, drag the appropriate settings to the correct devices. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You have a Windows 11 capable device named Device1 that runs the 64-bit version of
Windows 10 Enterprise and has Microsoft Office 2019 installed. You have the Windows 11
Enterprise images shown in the following table.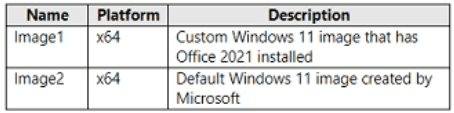
Which images can be used to perform an in-place upgrade of Device1?
A. image1 only
B. lmage2only
C. Image1 and Image2
You have a Microsoft 365 E5 subscription.
You create an app protection policy for Android devices named Policy1 as shown in the
following exhibit.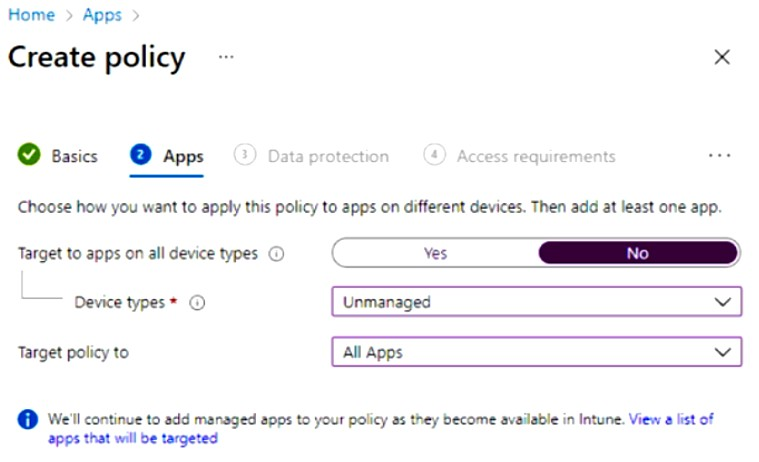
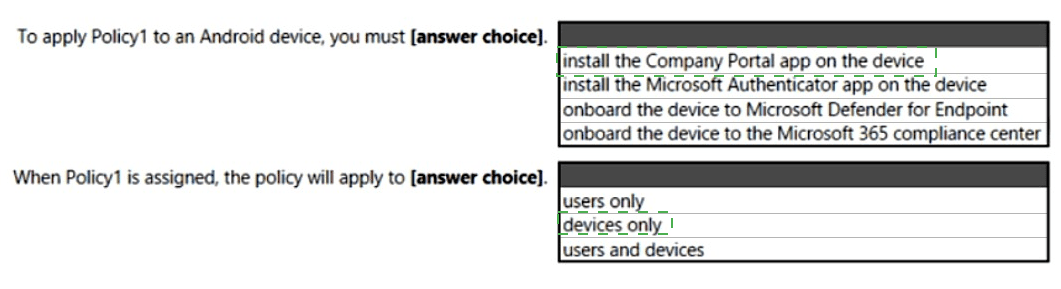
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.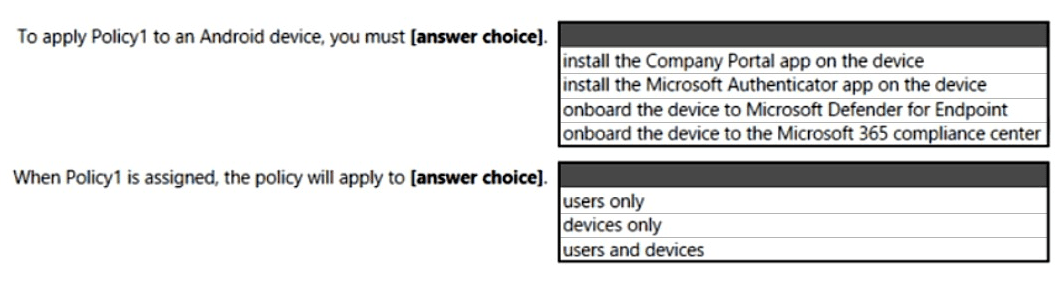
You have a Microsoft 365 subscription that includes Microsoft Intune.
You create a new Android app protection policy named Policy1 that prevents screen captures in all Microsoft apps. You discover that an unmanaged email client installed on Android devices can still capture screens You need to ensure that users can only use Microsoft apps to access email. What should you do?
A. Create a Conditional Access policy.
B. Create a compliance policy.
C. Modify the Data protection settings of Policy1.
D. Modify the assignments of Policy1.
You have a Microsoft 365 subscription that contains devices enrolled in Microsoft Intune.
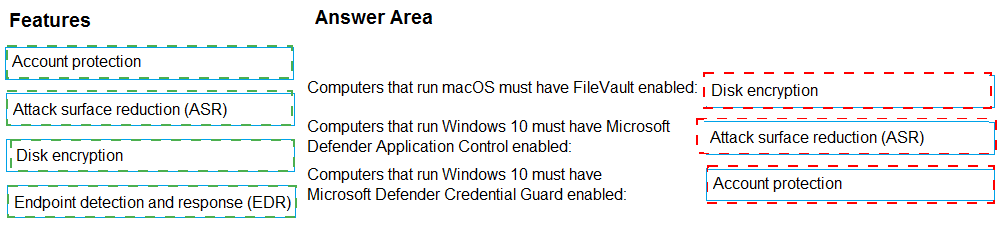
You need to create Endpoint security policies to enforce the following requirements:
• Computers that run macOS must have FileVault enabled.
• Computers that run Windows 10 must have Microsoft Defender Credential Guard
enabled.
• Computers that run Windows 10 must have Microsoft Defender Application Control
enabled.
Which Endpoint security feature should you use for each requirement? To answer, drag the
appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Your company has an infrastructure that has the following:
• A Microsoft 365 tenant
• An Active Directory forest
• Microsoft Intune
• A Key Management Service (KMS) server
• A Windows Deployment Services (WDS) server
• An Azure AD Premium tenant
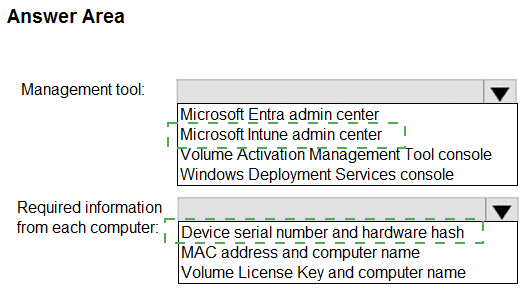
The company purchases 100 new client computers that run Windows.
You need to ensure that the new computers are joined automatically to Azure AD by using
Windows Autopilot.
What should you use? To answer, select the appropriate options in the answer area,
NOTE: Each correct selection is worth one point.
| Page 1 out of 32 Pages |