Topic 2: Litware inc

You have a Microsoft 365 subscription that contains two users named User1 and User2.
You need to ensure that the users can perform the following tasks:
• User1 must be able to create groups and manage users.
• User2 must be able to reset passwords for no administrative users.
The solution must use the principle of least privilege.
Which role should you assign to each user? To answer, drag the appropriate roles to the correct users. Each role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

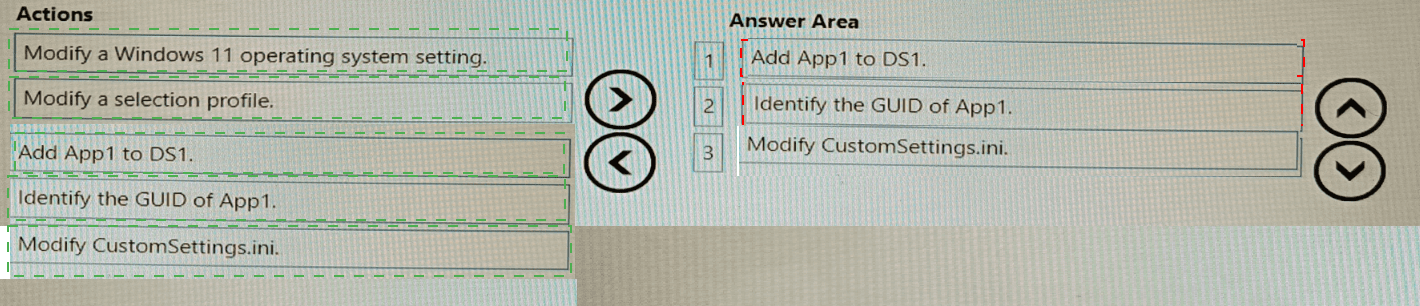
You have a Microsoft Deployment Toolkit (MDT) deployment share named DS1.
You import a Windows 11 image to DS1.
You have an executable installer for an application named App1.
You need to ensure that App1 will be installed for all the task sequences that deploy the image.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.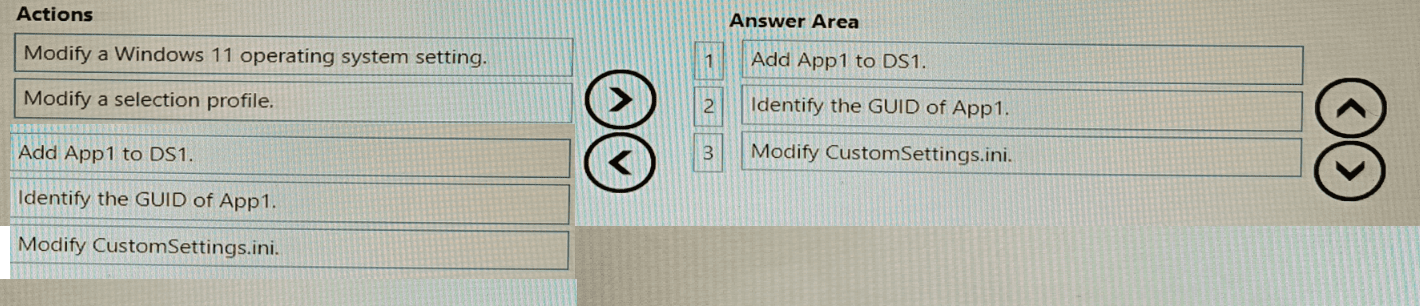
You have a Microsoft 365 subscription.
Users have iOS devices that are not enrolled in Microsoft 365 Device Management.
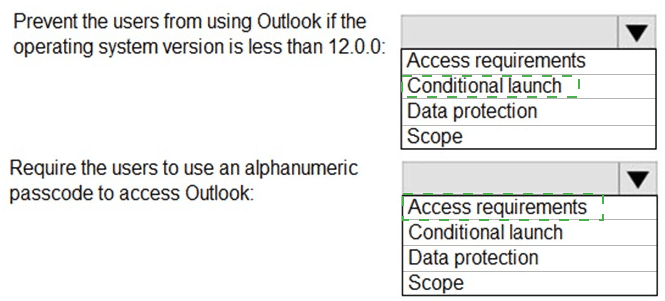
You create an app protection policy for the Microsoft Outlook app as shown in the exhibit. (Click the Exhibit tab.)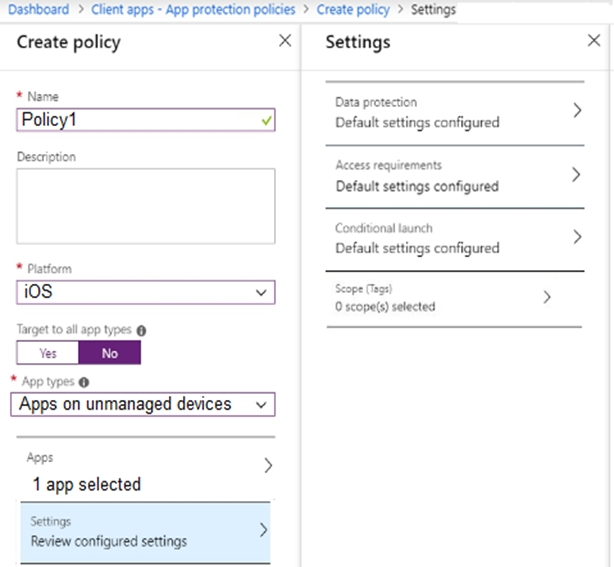
You need to configure the policy to meet the following requirements:
Prevent the users from using the Outlook app if the operating system version is less than 12.0.0.
Require the users to use an alphanumeric passcode to access the Outlook app.
What should you configure in an app protection policy for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.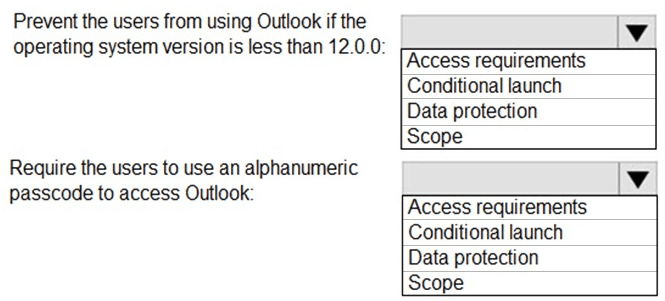
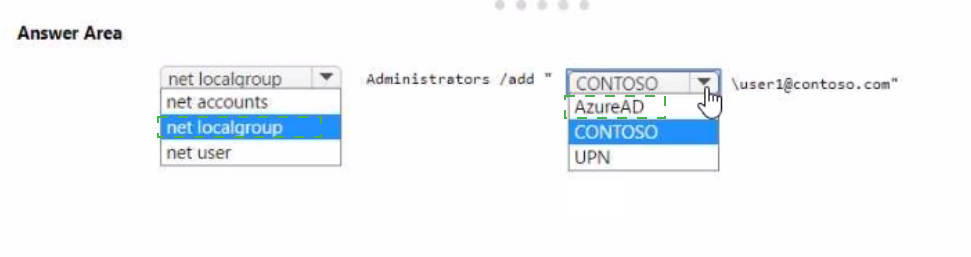
You have an Azure AD tenant named contoso.com that contains a user named Used. User! has a user principal name (UPN) of user1@contoso.com.
You join a Windows 11 device named Client 1 to contoso.com.
You need to add User1 to the local Administrators group of Client1.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.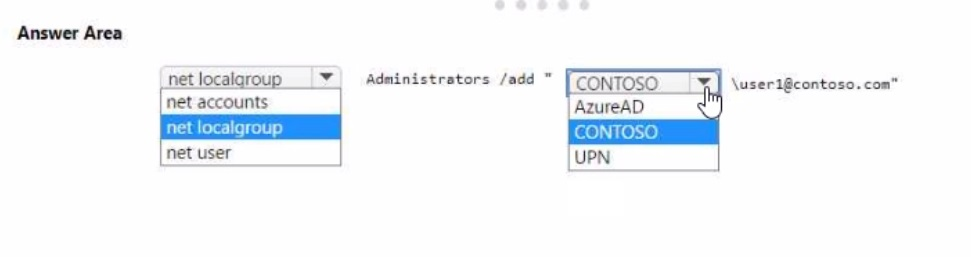
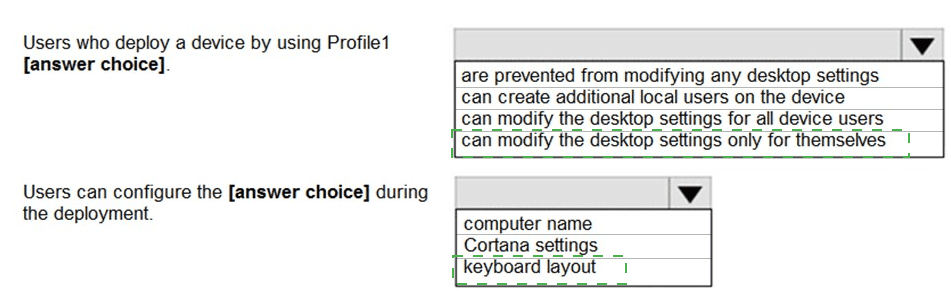
You have a Microsoft Intune subscription.
You are creating a Windows Autopilot deployment profile named Profile1 as shown in the
following exhibit.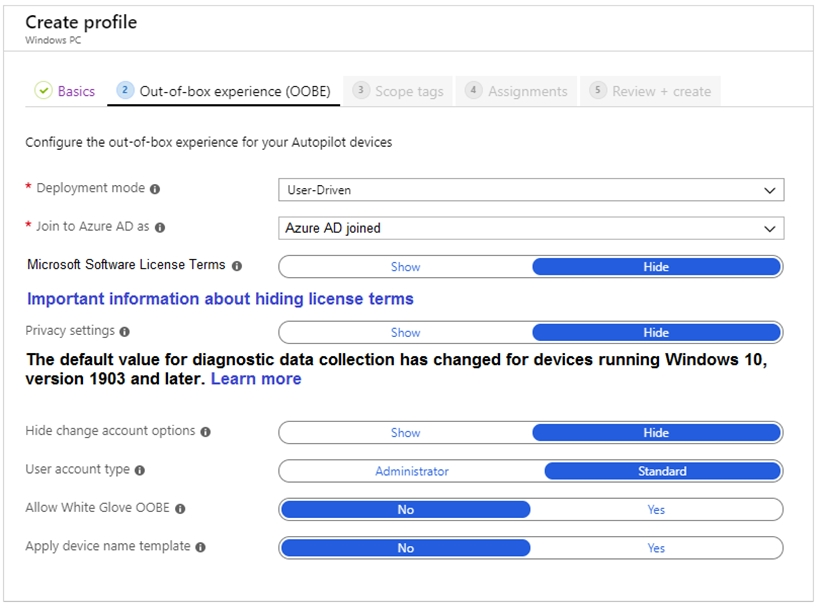
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.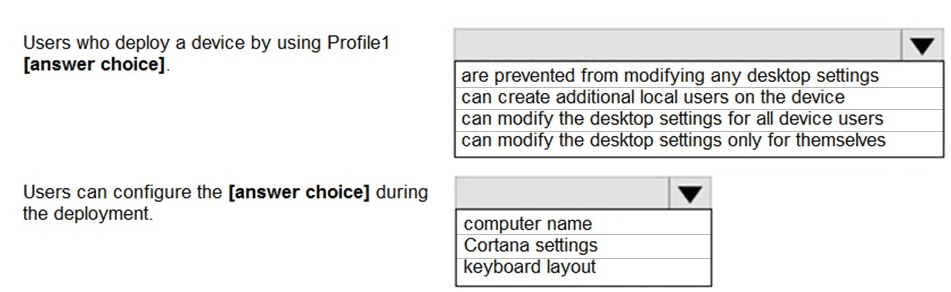
You have a computer named Computer! that runs Windows 11.
A user named User1 plans to use Remote Desktop to connect to Computer1.
You need to ensure that the device of User1 is authenticated before the Remote Desktop connection is established and the sign in page appears.
What should you do on Computer1?
A. Turn on Reputation-based protection.
B. Enable Network Level Authentication (NLA).
C. Turn on Network Discovery.
D. Configure the Remote Desktop Configuration service.
Your network contains an on-premises Active Directory domain. The domain contains two computers named Computer1 and Computer? that run Windows 10.
You install Windows Admin Center on Computer1.
You need to manage Computer2 from Computer1 by using Windows Admin Center.
What should you do on Computed?
A. Update the TrustedHosts list
B. Run the Enable-PSRemoting cmdlet
C. Allow Windows Remote Management (WinRM) through the Microsoft Defender firewall.
D. Add an inbound Microsoft Defender Firewall rule.
You have groups that use the Dynamic Device membership type as shown in the following
table.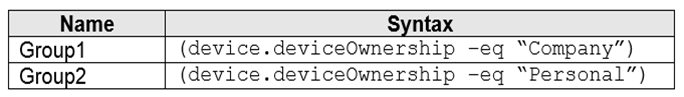
You are deploying Microsoft 365 apps.
You have devices enrolled in Microsoft Intune as shown in the following table.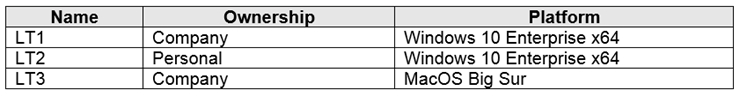
In the Microsoft Endpoint Manager admin center, you create a Microsoft 365 Apps app as
shown in the exhibit. (Click the Exhibit tab.)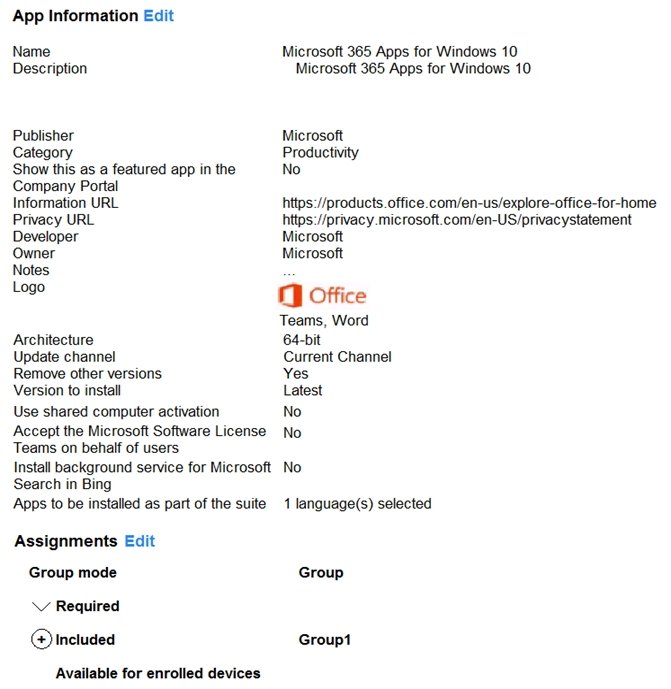 For each of the following statements, select Yes if the statement is true. Otherwise, select No.
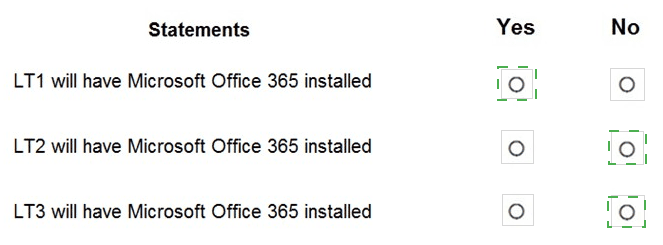
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
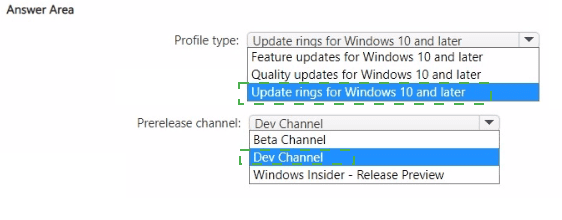
You have a Microsoft 365 E5 subscription. All devices are enrolled in Microsoft Intune.
You have a device group named Group1 that contains five Windows 11 devices.
You need to ensure that the devices in Group1 automatically receive new Windows 11 builds before the builds are released to the public.
What should you configure in Intune? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.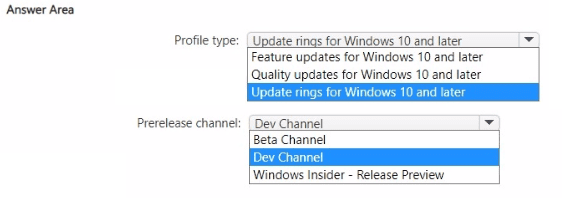
Your network contains an Active Directory domain named contoso.com. The domain contains two computers named Computer! and Computer2 that run Windows 10. On Computer1, you need to run the Invoke-Command cmdlet to execute several PowerShell commands on Computed. What should you do first?
A. On Computed, run the Enable-PSRemoting cmdlet.
B. On Computed, add Computer! to the Remote Management Users group.
C. From Active Directory, configure the Trusted for Delegation setting for the computer account of Computed.
D. On Computer1, run the HcK-PSSession cmdlet.
| Page 2 out of 32 Pages |