Topic 4: Misc. Questions
Your on-premises network contains an Active Directory domain that uses Microsoft Entra
Connect to sync with a Microsoft Entra tenant.
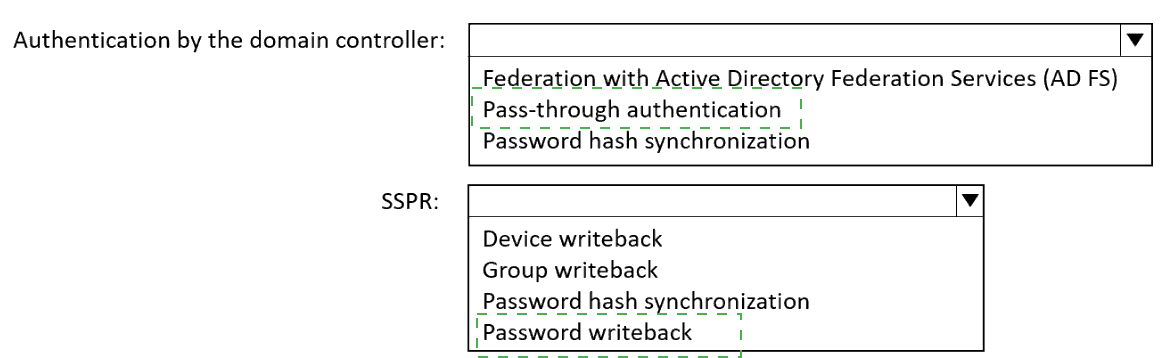
You need to configure Microsoft Entra Connect to meet the following requirements:
Microsoft Entra sign-ins must be authenticated by an Active Directory domain controller.
Active Directory domain users must be able to use Microsoft Entra self-service password
reset (SSPR).
Minimize administrative effort.
What should you use for each requirement? To answer, select the appropriate options in
the answer area.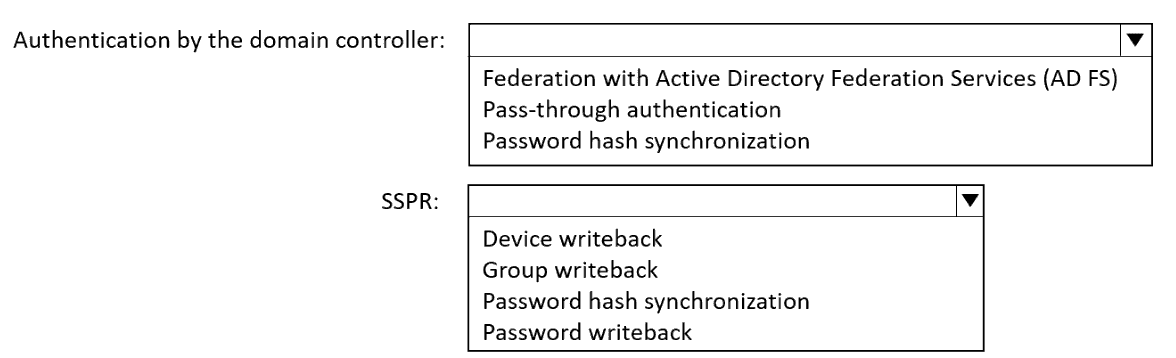
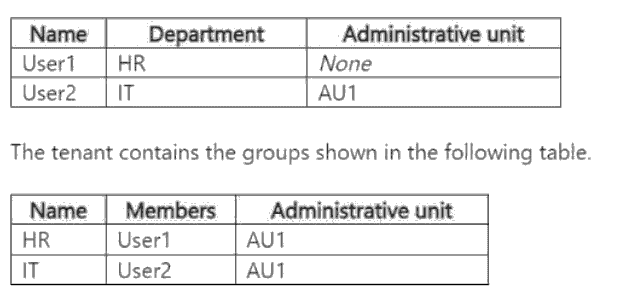
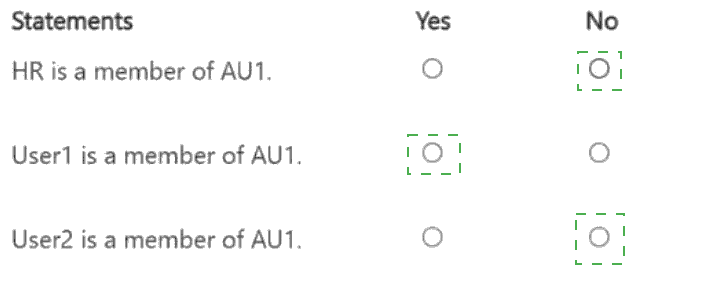
You have a Microsoft Entra tenant that contains an administrative unit named AU1. AU1 is
configured for assigned membership.
The tenant contains the users shown in the following table.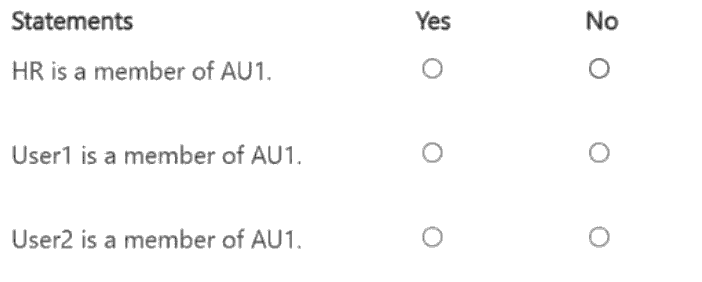
For AU1, you update the following configurations:
. Membership type: Dynamic User
· Dynamic membership rule: (user.department -eq "hr")
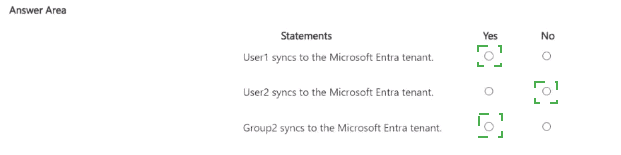
For each of the following statements, select Yes if the statement is true. Otherwise, select
No.
You have a Microsoft 365 E5 subscription.
You plan to deploy a third-party software as a service (SaaS) app named App1.
You need to onboard App1 to Microsoft Defender for Cloud Apps. The solution must
ensure that you can implement session control policies.
What should you do first?
A. From the Microsoft Defender portal, configure Cloud discovery.
B. From the Microsoft Entra admin center, configure a traffic forwarding profile.
C. From the Microsoft Entra admin center, configure single sign-on (SSO) for App1.
D. From the Microsoft Defender portal, create an OAuth app policy.
You have a Microsoft Entra tenant.
You have the end-user desktop environments shown in the following table.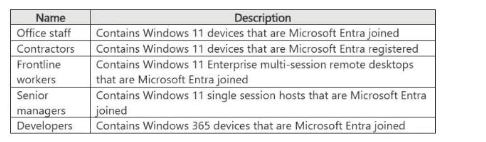
You need to deploy Global Secure Access.
In which environments can you install the Global Secure Access client?
A. Developers, Office staff, and Senior managers only
B. Contractors, Developers, Frontline workers. Office staff, and Senior managers
C. Frontline workers and Senior managers only
D. Contractors and Office staff only
You have on-premises Linux devices.
You have a Microsoft 365 E5 subscription.
You plan to configure Global Secure Access Internet Access.
You need to ensure that the devices can connect to Global Secure Access.
What should you do?
A. Deploy a private network connector.
B. Configure the Adaptive Access settings.
C. Install the Azure Connected Machine agent on the devices.
D. Create a remote network.
You have a Microsoft 365 E5 subscription.
You have an Azure subscription that is linked to a Microsoft Entra tenant. The tenant
contains a user named User1.
You plan to deploy Microsoft Entra Permissions Management.
You need to ensure that User1 can onboard the Azure subscription to Permissions
Management. The solution must follow the principle of least privilege.
Which Microsoft Entra role should you assign to User1?
A. Security Administrator
B. Application Administrator
C. Permissions Management Administrator
D. Global Administrator
Your network contains an on premises Active Directory domain named conIoso.com. The
domain contains the objects shown in the following table.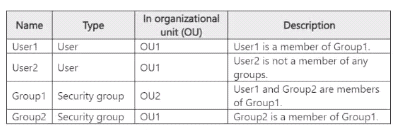
You install Microsoft Entra Connect. You configure the Domain and OU filtering settings as
shown in the Domain and OU filtering exhibit. (Click the domain and OU Filtering tab.)
You configure the Filter user and devices settings as shown in the Filter Users and Devices
exhibit. (Click the filter Users and Devices tab).
For each of the following statements, select Yes if the statement is true. Otherwise, select
No.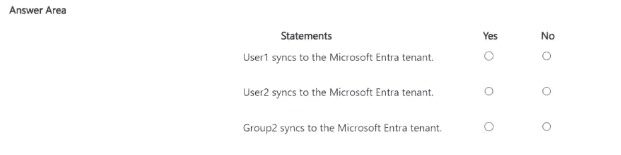
You have a Microsoft Entra tenant that contains the users shown in the following table: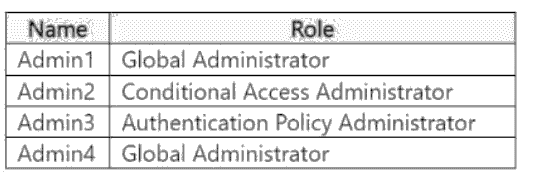
Admin4 creates a Conditional Access policy named Policy1 by using the "Require
multifactor authentication for Azure management" template.
Which users will be required to use multi-factor authentication (MFA) the next time they
sign in?
A. Admin2 and Admin3 only
B. Admin1 and Admin4 only
C. Admin1, Admin2, and Admin3 only
D. Admin1, Admin2, Admin3, and Admin4
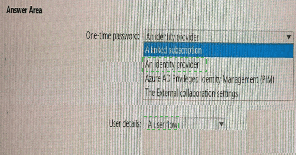
You have an Azure AD tenant and an Azure web app named App1.
You need to provide guest users with self-service sign-up for App1. The solution must meet
the following requirements:
• Guest users must be able to sign up by using a one-time password.
• The users must provide their first name, last name, city, and email address during the
sign-up process.
What should you configure in the Azure Active Directory admin center for each
requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.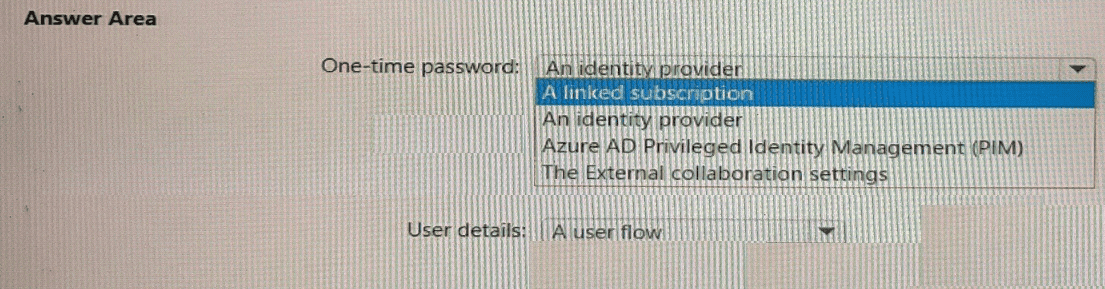
You have a Microsoft 365 tenant
You currently allow email clients that use Basic authentication to connect to Microsoft
Exchange Online.
You need to ensure that users can connect to Exchange Online only from email clients that
use Modern authentication protocols.
What should you implement?
A. a Microsoft Defender for Cloud Apps OAuth policy
B. a Microsoft Intune app protection policy
C. a Microsoft Intune compliance policy
D. a Microsoft Entra conditional access policy
| Page 4 out of 36 Pages |