Topic 3: Misc. Questions
You deploy Azure Sentinel.
You need to implement connectors in Azure Sentinel to monitor Microsoft Teams and Linux
virtual machines in Azure. The solution must minimize administrative effort.
Which data connector type should you use for each workload? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Explanation:
The question asks for the data connector type that minimizes administrative effort for ingesting logs from Microsoft Teams and Linux VMs into Azure Sentinel. Microsoft provides built-in, agentless data connectors for many Azure and Microsoft 365 services, which require the least configuration. For resources where no built-in connector exists, a custom or agent-based approach is needed.
Correct Option:
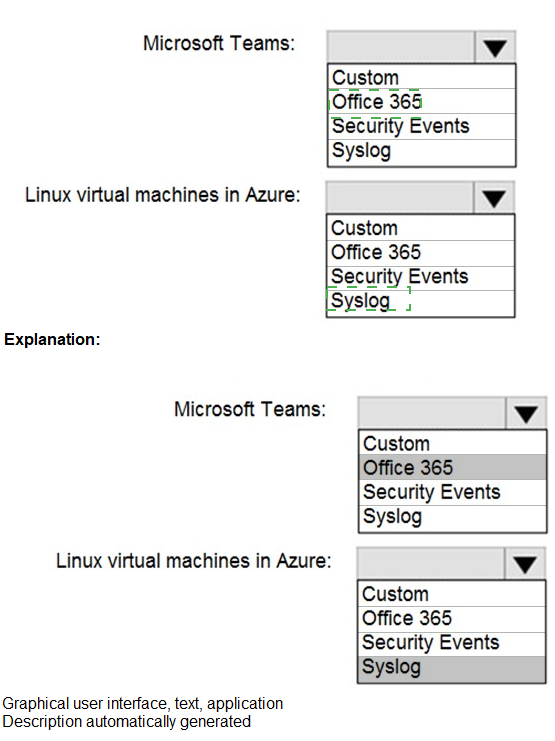
Microsoft Teams:
Office 365. The Office 365 data connector is a built-in, agentless connector that ingests audit and activity logs from Microsoft 365 services, including Microsoft Teams. It only requires a global admin to consent to the connection, minimizing effort.
Linux virtual machines in Azure:
Syslog. The most efficient way to collect common Linux logs (like auth.log, syslog) is by installing the Log Analytics agent (AMA agent) on the VM and configuring the Syslog data connector in Sentinel. This centralizes configuration in Sentinel and leverages the existing agent framework, minimizing per-VM manual effort compared to a fully custom solution.
Incorrect Option:
Custom:
Using a custom connector (like via Logic Apps, Functions, or the REST API) for these workloads would introduce unnecessary development, maintenance, and configuration overhead when purpose-built, managed connectors exist.
Security Events:
This connector is specific to collecting Windows Security events (Event IDs) via the Log Analytics agent. It is not the appropriate or efficient choice for Microsoft Teams cloud logs or general Linux system logs.
(For Linux VMs) Office 365:
This connector is only for Microsoft 365 cloud services and cannot be applied to Linux virtual machines in Azure.
Reference:
Microsoft Learn, "Connect data sources" - Specifically, documentation on the Office 365 connector and collecting data from Linux computers using the Log Analytics agent and Syslog.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender and an Azure
subscription that uses Azure Sentinel.
You need to identify all the devices that contain files in emails sent by a known malicious
email sender. The query will be based on the match of the SHA256 hash.
How should you complete the query? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Explanation:
This Kusto Query Language (KQL) question requires creating an efficient join between two tables to find devices where email attachment hashes match file hashes on devices. The goal is to identify the correct join key and the required fields from each table. A join should use a unique, common key present in both tables for accurate results, which in this case is the SHA256 hash.
Correct Option:
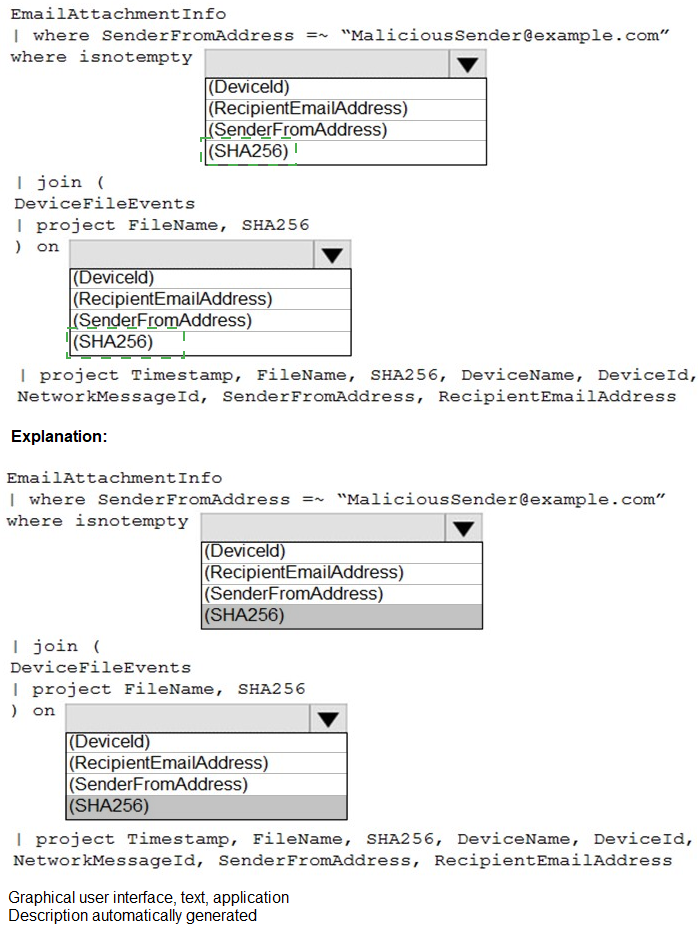
The correct sequence to complete the query is:
where isnotempty(SHA256) -
This filters the EmailAttachmentInfo table to only rows that have a hash value, which is essential for a valid join.
on SHA256 -
The join between EmailAttachmentInfo and DeviceFileEvents must be performed on the common SHA256 hash field to correlate attachments with files on devices.
project FileName, SHA256 -
Before the join, the sub-query for DeviceFileEvents should project (select) the SHA256 (the join key) and the FileName for clarity in the final results. The SHA256 field is mandatory to keep for the join operation to succeed.
Incorrect Option:
(DeviceId), (RecipientEmailAddress), (SenderFromAddress) for the where isnotempty() clause:
While these fields exist in EmailAttachmentInfo, filtering on them here is incorrect. The goal is to join on hash, so we must ensure the hash field (SHA256) itself is not empty for the join to be possible and meaningful.
(DeviceId), (RecipientEmailAddress), (SenderFromAddress) as the join key:
These fields are not common to both the EmailAttachmentInfo and DeviceFileEvents tables. Using them for the join operation would result in no matches or incorrect correlations. The only reliable common identifier for a file/attachment is its SHA256 hash.
Reference:
Microsoft Learn, "KQL Quick Reference" and "Join operators" - Emphasizes that joins require a common key between tables, and the SHA256 field is the standard identifier for files across Microsoft 365 Defender tables like EmailAttachmentInfo and DeviceFileEvents.
You have an Azure subscription that uses Azure Defender.
You plan to use Azure Security Center workflow automation to respond to Azure Defender
threat alerts.
You need to create an Azure policy that will perform threat remediation automatically.
What should you include in the solution? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Explanation:
The question is about using Azure Policy's DeployIfNotExists effect to automatically remediate non-compliance, triggered by Azure Security Center (ASC) alerts. Workflow automation in ASC can launch a Logic App in response to an alert. The policy effect must be able to deploy resources to enforce state, and the automation must be triggered by the alert itself, not a manual response action.
Correct Option:
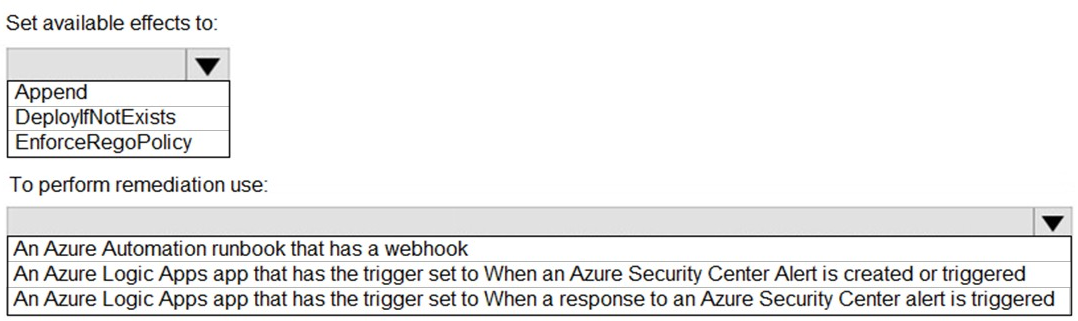
Set available effects to:
DeployIfNotExists. This policy effect evaluates resources and, if they are non-compliant, automatically deploys a remediation template (like an ARM template) to bring them into the desired state. It's the appropriate effect for automated remediation triggered by policy evaluation related to a security alert.
To perform remediation use:
An Azure Logic Apps app that has the trigger set to When an Azure Security Center Alert is created or triggered. This is the correct workflow automation trigger. It allows the Logic App to run automatically as soon as ASC generates a threat alert, which can then execute remediation steps (like calling APIs to fix the issue).
Incorrect Option:
Append:
This effect adds additional parameters/fields to a resource during creation but does not modify existing non-compliant resources or deploy remediation templates. It is not used for active remediation.
EnforceRegoPolicy:
This effect is specific to Gatekeeper v3 and policies for Kubernetes (AKS), not for general Azure resource remediation tied to ASC alerts.
An Azure Automation runbook that has a webhook:
While Automation runbooks can be triggered via webhooks, this is not the native, integrated trigger for ASC workflow automation. It adds unnecessary complexity.
An Azure Logic Apps app that has the trigger set to When a response to an Azure Security Center alert is triggered:
This trigger is for initiating a manual playbook response from within the alert incident page in Sentinel or ASC. It does not provide automatic remediation upon alert generation.
Reference:
Microsoft Learn, "Remediate non-compliant resources with Azure Policy" and "Automate responses to Security Center triggers". The DeployIfNotExists effect is documented for remediation, and the "When an Azure Security Center alert is created or triggered" is the standard Logic App trigger for alert-based automation.
You have the following KQL query.

Explanation:
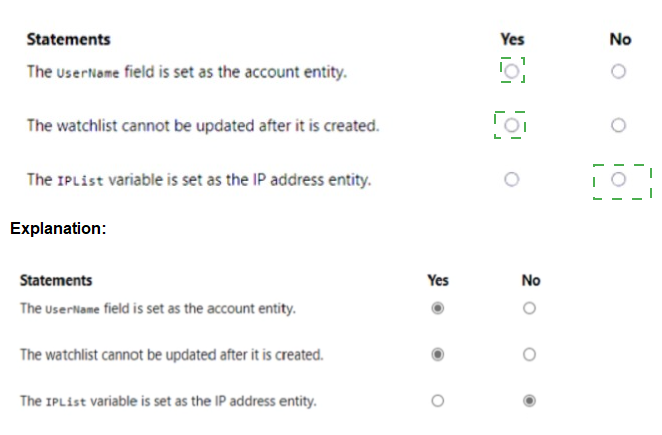
This question tests the ability to interpret a Kusto Query Language (KQL) query used in Azure Sentinel, focusing on entity mapping and watchlist properties. The query uses a watchlist named 'Bad_IPs', parses Sysmon network events, and compares IPs against that list. The three statements must be evaluated as true (Yes) or false (No) based on standard KQL and Azure Sentinel functionality.
Correct Option:
The correct answers for each statement are:
"The userName field is set as the account entity.":
Yes. The query line AccountCustomEntity = UserName explicitly maps the UserName field to the built-in AccountCustomEntity placeholder, which tells Sentinel to treat this value as the Account entity for incident enrichment.
"The watchlist cannot be updated after it is created.":
No. This statement is false. Watchlists in Azure Sentinel are designed to be updated. You can add, modify, or delete items in a watchlist after its creation, and queries using them will reflect the latest data.
"The IPList variable is set as the IP address entity.":
No. This statement is false. The IPList variable is populated with data from a watchlist (_GetWatchlist('Bad_IPs')) for use in the in clause. It is not mapped to a Sentinel entity. The query maps SourceIP/DestinationIP fields to the output but does not use the IPCustomEntity placeholder (e.g., IPCustomEntity = SourceIP) to formally identify them as IP address entities for incident creation.
Incorrect Option:
(For statement 1) Saying "No" would be incorrect because the AccountCustomEntity = UserName assignment is a direct and correct example of entity mapping in a Sentinel query.
(For statement 2) Saying "Yes" would be incorrect because it contradicts the core, documented feature of watchlists being updatable data sources.
(For statement 3) Saying "Yes" would be incorrect.While the query uses IP addresses, the variable IPList contains the watchlist data. Entity mapping requires using specific built-in entity identifiers like IPCustomEntity in the query's extend or project clause, which is not done here for the IPList variable itself.
Reference:
Microsoft Learn, "Map data fields to entities in Azure Sentinel" and "Use watchlists in Azure Sentinel". Documentation shows that entity mapping uses specific column names (e.g., AccountCustomEntity) and that watchlists support CRUD operations via the portal, API, or manual edit.
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to configure Azure Security Center to detect possible threats related to sign-ins
from suspicious IP addresses to Azure virtual machines. The solution must validate the
configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate
actions from the list of action to the answer area and arrange them in the correct order.
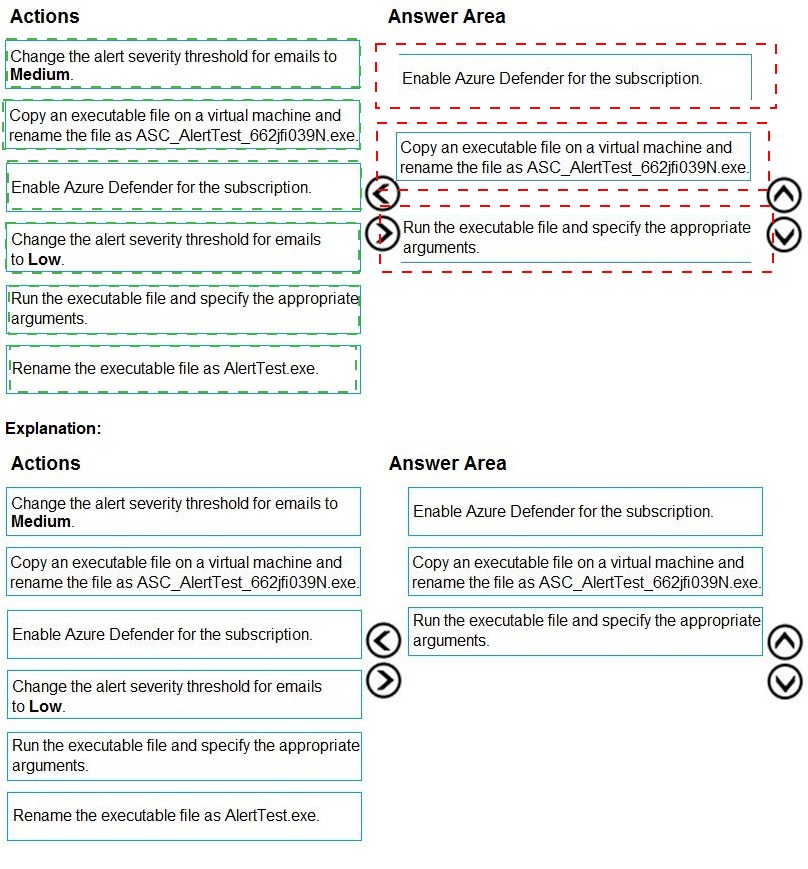
Explanation:
The goal is to enable threat detection for Azure VMs and then validate that alerts are generated. Azure Defender (now Microsoft Defender for Cloud) provides the threat detection capabilities. The standard validation method is to simulate an attack using the provided test alert tool (a specific executable with specific arguments and naming) which triggers a sample alert.
Correct Option:
The correct sequence of actions is:
Enable Azure Defender for the subscription. This is the foundational step. Azure Defender is required for its advanced threat detection features, including alerts for suspicious sign-ins to VMs. Without it enabled, no threat alerts will be generated.
Copy an executable file on a virtual machine and rename the file as ASC_AlertTest_662jfi039N.exe. This is the first step of the validation test. You must place the test file on a VM and rename it to the exact, unique name that the Azure Security Center alert simulation expects.
Run the executable file and specify the appropriate arguments. After renaming the file correctly, you execute it with the required arguments (e.g., -Attack). This simulates malicious activity and should trigger a test alert in Security Center, confirming the configuration works.
Incorrect Option:
Change the alert severity threshold for emails to Medium/Low:
These actions are unrelated. The question is about detecting threats on Azure virtual machines, not configuring email notification filters for alerts. Severity thresholds for emails are for tuning notifications, not enabling or validating the underlying detection.
Rename the executable file as AlertTest.exe:
This is incorrect. The validation test requires the specific filename ASC_AlertTest_662jfi039N.exe. Using a generic name like AlertTest.exe will not trigger the expected test alert from Microsoft's detection rules.
(Any sequence not starting with Enable Azure Defender):
Enabling Azure Defender is the mandatory prerequisite. No threat detection or validation can occur without it.
Reference:
Microsoft Learn, "Azure Security Center - Setting up Azure Defender" and "Alert validation in Azure Security Center". The validation procedure specifically documents downloading, renaming to the precise ASC_AlertTest* name, and running the executable with arguments.
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that
affects your environment.
You need to use Microsoft Defender Security Center to request remediation from the team
responsible for the affected systems if there is a documented active exploit available.
Which three actions should you perform in sequence? To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.
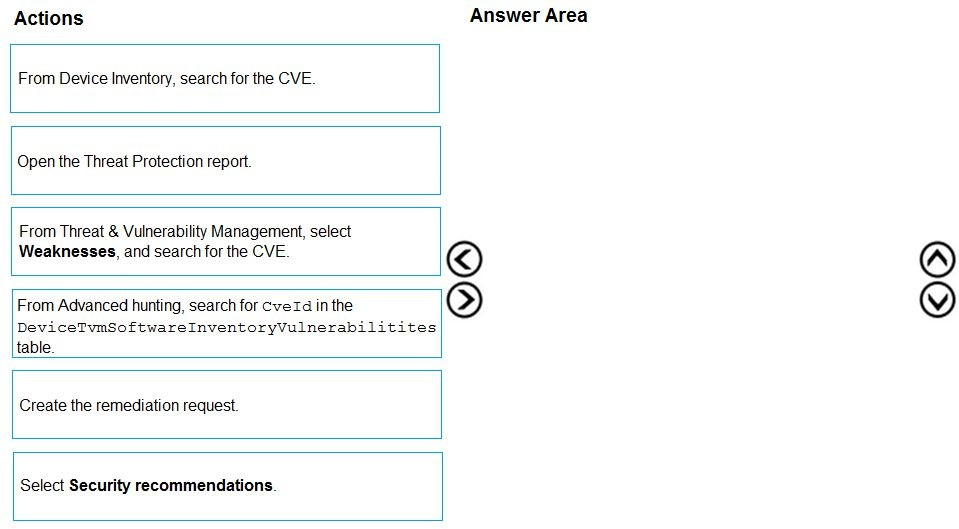
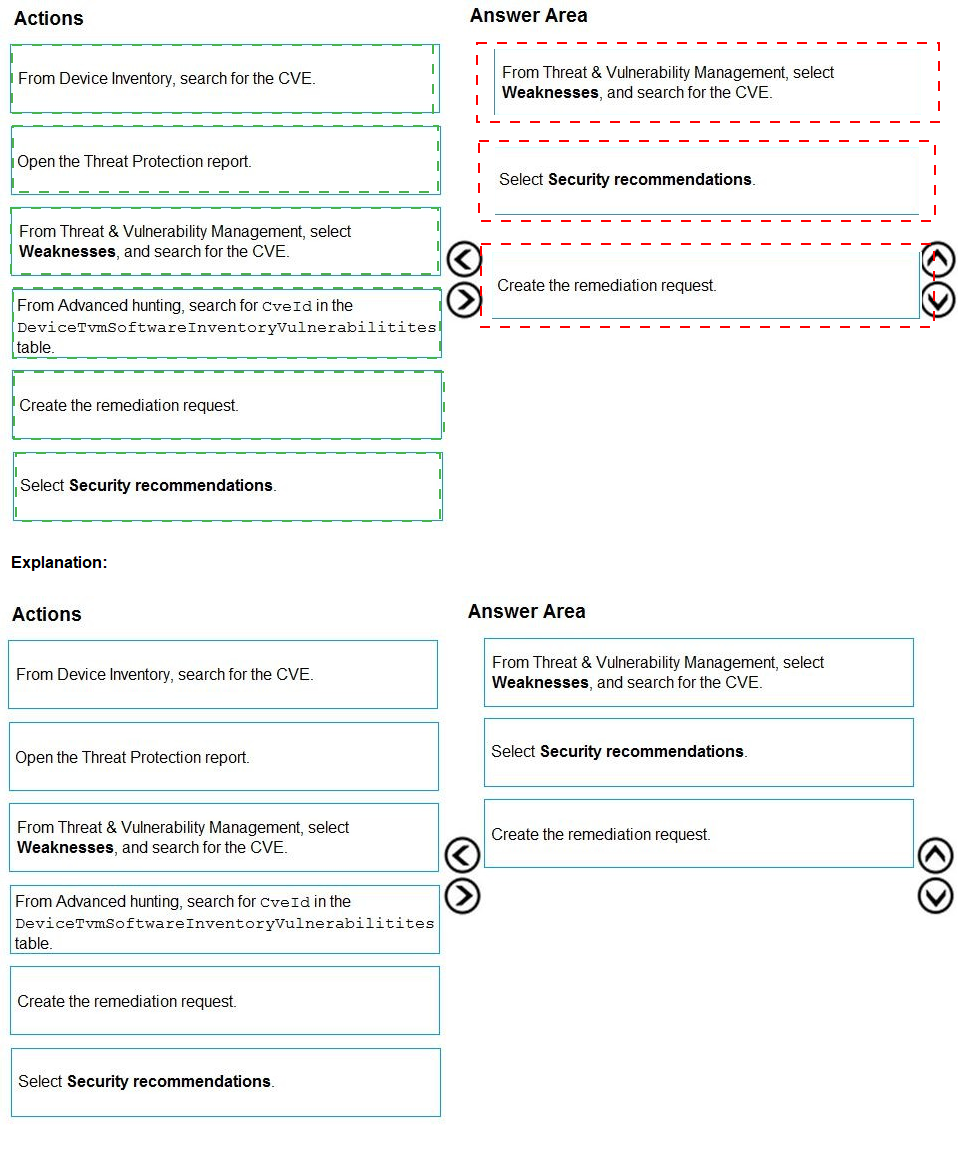
Explanation:
The task is to find a specific CVE in Microsoft Defender for Endpoint's Threat & Vulnerability Management (TVM) module, check for active exploit availability, and then initiate remediation. The process follows the standard workflow within the Microsoft Defender Security Center portal, starting with the dedicated vulnerability management section, drilling down to details, and taking action.
Correct Option:
The correct sequence of actions is:
From Threat & Vulnerability Management, select Weaknesses, and search for the CVE. This is the primary interface for investigating known software vulnerabilities (CVEs). The "Weaknesses" tab is where you search for and select a specific CVE to view its details.
From Advanced hunting, search for CveId in the DeviceTvmSoftwareInventoryVulnerabilities table. After locating the CVE in the UI, you need to verify if there is a documented active exploit. The Advanced Hunting tool, specifically the DeviceTvmSoftwareInventoryVulnerabilities table, provides the most detailed and queryable data, including the ExploitabilityLevel field which indicates if an exploit is publicly available.
Create the remediation request. Once you have confirmed the CVE affects your environment and have verified the exploit context (e.g., from the Advanced Hunting data or the CVE details page which also shows this info), you can proceed to create a remediation request (exposure task) for the responsible team directly from the CVE's page.
Incorrect Option:
From Device Inventory, search for the CVE:
Device Inventory is for searching devices, not vulnerabilities. It is not the correct starting point for finding CVE details.
Open the Threat Protection report:
This is a general dashboard for viewing alerts and overall security posture, not the specialized tool for vulnerability management and CVE investigation.
Select Security recommendations:
While related, "Security recommendations" is a broader list of hardening suggestions. It may contain items related to the CVE, but it is not the most direct way to search for a specific CVE ID and its exploit details to initiate a targeted remediation request.
Reference:
Microsoft Learn, "Threat and Vulnerability Management in Microsoft Defender for Endpoint - Vulnerability pages" and "Use advanced hunting to track vulnerabilities". The documented workflow involves navigating to the TVM Weaknesses page, and advanced hunting is recommended for detailed vulnerability data analysis.
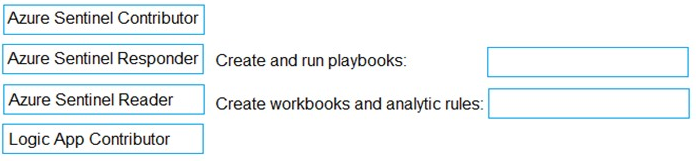
Your company deploys Azure Sentinel.
You plan to delegate the administration of Azure Sentinel to various groups.
You need to delegate the following tasks:
Create and run playbooks
Create workbooks and analytic rules.
The solution must use the principle of least privilege.
Which role should you assign for each task? To answer, drag the appropriate roles to the
correct tasks. Each role may be used once, more than once, or not at all. You may need to
drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
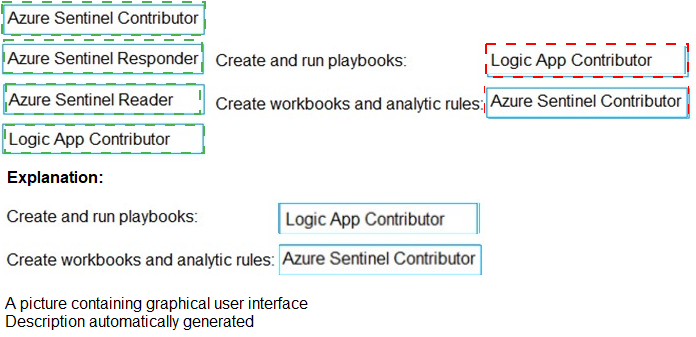
Explanation:
This question is about applying the principle of least privilege when assigning Azure built-in roles for specific Azure Sentinel administrative tasks. The roles must grant only the permissions necessary to perform the defined task and nothing more.
Correct Option:
Task: Create and run playbooks → Role: Logic App Contributor
Playbooks in Azure Sentinel are built on Azure Logic Apps. The Logic App Contributor role allows users to create, manage, and run Logic Apps (playbooks) but does not grant permissions to modify Azure Sentinel resources like analytics rules or incidents. This is the perfect least-privilege role for managing playbooks.
Task: Create workbooks and analytic rules → Role: Azure Sentinel Contributor
The Azure Sentinel Contributor role is specifically designed for this purpose. It grants full permissions to create, edit, and manage all Azure Sentinel resources, including workbooks, analytics rules, data connectors, and incidents. It is more granular than a global contributor role but provides the necessary scope for these two tasks within Sentinel.
Incorrect Option:
Azure Sentinel Responder:
This role only allows a user to view data, incidents, and perform investigative actions (like closing incidents). It does not grant permissions to create resources like workbooks or analytic rules.
Azure Sentinel Reader:
This is a view-only role. It allows viewing data, incidents, dashboards, and rules but prohibits making any changes or creating new resources.
Logic App Contributor (for creating workbooks/rules):
While this role is correct for playbooks, it is incorrect for creating Sentinel workbooks and analytic rules. The Logic App Contributor role has no permissions on Azure Sentinel resources themselves.
Reference:
Microsoft Learn, "Permissions in Azure Sentinel". The documentation clearly defines the scope of each built-in role: Azure Sentinel Contributor can create and manage all Sentinel artifacts, while Logic App Contributor is required to manage the underlying Logic Apps resources used for automation.
You have an Azure subscription. The subscription contains 10 virtual machines that are
onboarded to Microsoft Defender for Cloud.
You need to ensure that when Defender for Cloud detects digital currency mining behavior
on a virtual machine, you receive an email notification. The solution must generate a test
email.
Which three actions should you perform in sequence? To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.

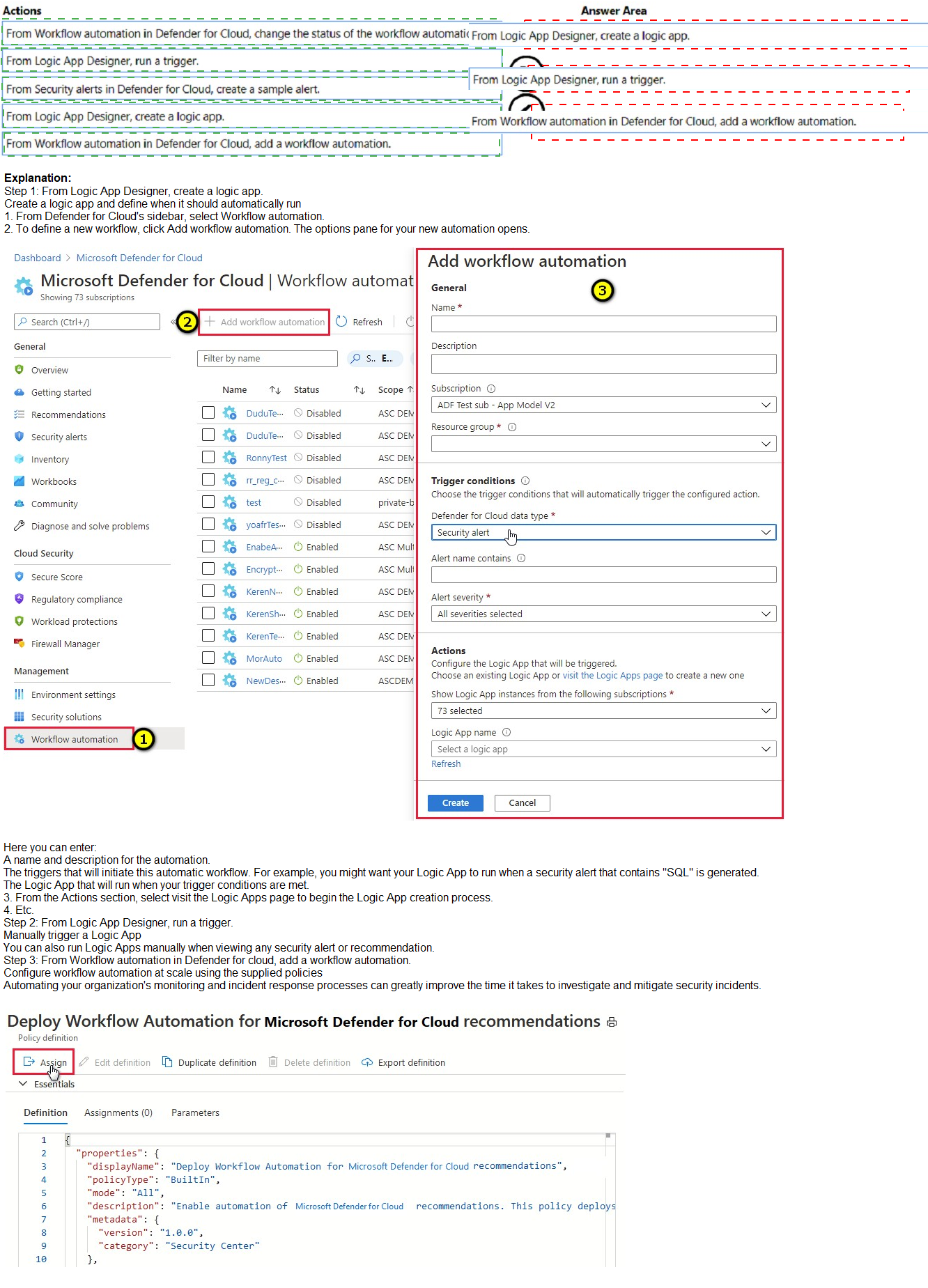
Explanation:
The goal is to configure automatic email notifications for a specific alert from Microsoft Defender for Cloud (MDC). This is done using the Workflow Automation feature, which uses Azure Logic Apps. The process involves creating the automation logic, setting up the trigger to an alert, and then testing it.
Correct Option:
The correct sequence of actions is:
From Logic App Designer, create a logic app. This is the first step to build the notification workflow. You create a new Logic App resource that will contain the steps to send an email (e.g., using the Office 365 Outlook connector).
From Workflow automation in Defender for Cloud, add a workflow automation. After creating the Logic App, you must connect it to Defender for Cloud. You create a new Workflow Automation in MDC, link it to the specific alert rule "Digital currency mining behavior detected", and select the newly created Logic App as the action to trigger.
From Security alerts in Defender for Cloud, create a sample alert. To generate a test email, you use the built-in "Create sample alerts" feature in Defender for Cloud. This simulates an alert, which will trigger your workflow automation and run the Logic App, sending the test email to validate the entire configuration.
Incorrect Option:
From Workflow automation in Defender for Cloud, change the status of the workflow automation:
This implies enabling/disabling an existing automation, not the initial creation and configuration steps.
From Logic App Designer, run a trigger:
You cannot manually "run a trigger" from the designer in this context. The trigger ("When a Microsoft Defender for Cloud alert is generated") is activated automatically by Defender for Cloud when an alert occurs. Testing is done by generating a sample alert from MDC.
(Any sequence that does not start with creating the Logic App):
The Logic App is the core component that performs the action (sending email). It must be created before it can be selected in the Workflow Automation configuration.
Reference:
Microsoft Learn, "Automate responses to Microsoft Defender for Cloud triggers". The documented workflow is: 1. Create a Logic App with the appropriate trigger and action. 2. In Defender for Cloud, create a Workflow Automation rule tied to a specific alert. 3. Use the "Create sample alerts" option to test the automation.
You manage the security posture of an Azure subscription that contains two virtual
machines name vm1 and vm2.
The secure score in Azure Security Center is shown in the Security Center exhibit. (Click
the Security Center tab.)
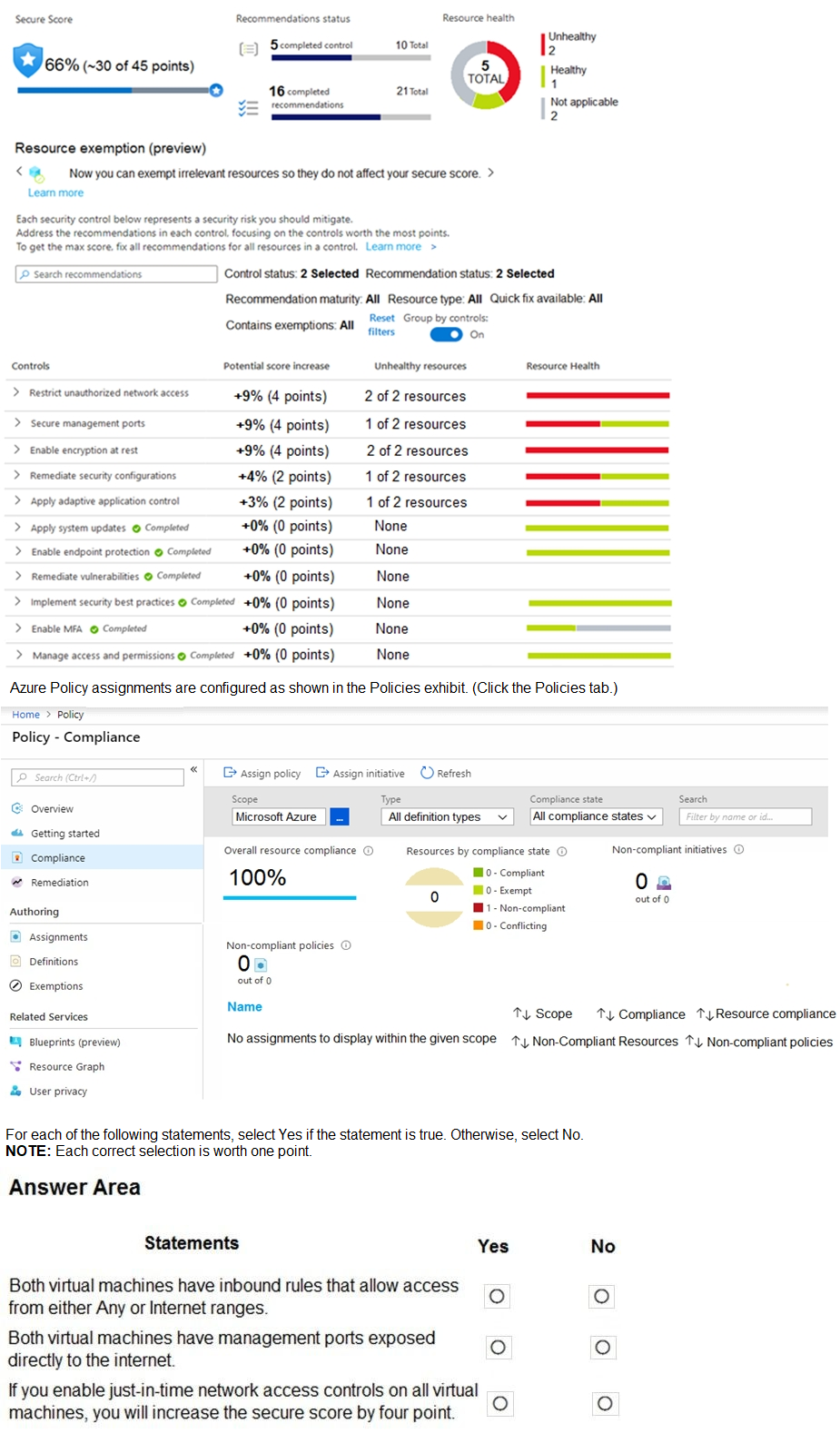
Explanation:
This question requires analyzing the Azure Security Center secure score breakdown and connecting it to policy compliance and potential remediation actions. The secure score increase percentages shown correspond to fully remediating specific security controls. We must deduce the current state of the VMs from the "unhealthy resources" counts and the potential score impact of enabling Just-In-Time (JIT) VM access.
Correct Option:
Both virtual machines have inbound rules that allow access from either Any or Internet ranges:
Yes. The control "Restrict unauthorized network access" shows 2 of 2 resources unhealthy, with a potential +9% (4 points) increase. This control typically flags NSG rules with overly permissive source IPs (like 'Any' or 'Internet'). Since both VMs are unhealthy, this statement is true.
Both virtual machines have management ports exposed directly to the internet:
No. The control "Secure management ports" shows 1 of 2 resources unhealthy, with a potential +9% (4 points) increase. This means only one VM (vm1 or vm2) has its management ports (e.g., RDP 3389, SSH 22) exposed to the internet. The statement says "both," which is false.
If you enable just-in-time network access controls on all virtual machines, you will increase the secure score by four points:
Yes. The "Secure management ports" control has a potential increase of +9% (which equals 4 points, as 45 total points * 9% ≈ 4 points). Enabling JIT on all VMs directly remediates the "Secure management ports" recommendation. Since one VM is already compliant, enabling JIT on the remaining unhealthy VM would fully satisfy the control, earning the full 4-point increase.
Incorrect Option:
Statement 1 = No:
This would be incorrect because the data shows 2/2 resources are unhealthy for the network access control, indicating a problem exists on both VMs.
Statement 2 = Yes:
This is incorrect because the data clearly shows only 1 of 2 resources is unhealthy for the management ports control, meaning the exposure does not apply to both VMs.
Statement 3 = No:
This is incorrect. The secure score increase is directly tied to controls. Fully remediating the "Secure management ports" control (by applying JIT to the non-compliant VM) would claim the entire potential score increase listed for that control, which is 4 points (9% of ~45).
Reference:
Microsoft Learn, "Secure score in Azure Security Center" and "Protect your management ports with just-in-time access." The secure score dashboard shows unhealthy resource counts per control, and JIT is the prescribed remediation for the "Secure management ports" recommendation.
You have an Azure subscription linked to an Azure Active Directory (Azure AD) tenant. The
tenant contains two users named User1 and User2.
You plan to deploy Azure Defender.
You need to enable User1 and User2 to perform tasks at the subscription level as shown in
the following table.
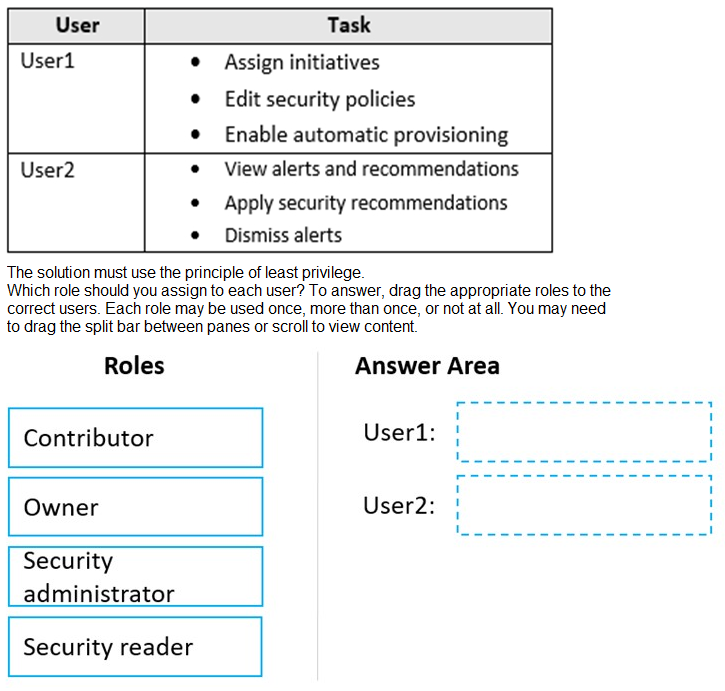
Explanation:
This question applies the principle of least privilege to assign Azure Active Directory (Azure AD) built-in roles at the subscription level. The roles must grant only the permissions necessary for the listed tasks. The key distinction is that User1 needs permissions to configure security settings (policies, provisioning), while User2 only needs permissions to view and act on existing security data (alerts, recommendations) without changing the underlying configuration.
Correct Option:
User1: Security administrator
The Security administrator role grants permissions to manage security components, including viewing and updating security policies, assigning initiatives (policy sets), and configuring security settings like auto-provisioning of agents. It does not grant full subscription management rights like Owner or Contributor, making it the least-privilege role for these configuration tasks.
User2: Security reader
The Security reader role is a view-only role with limited action permissions. It allows users to view security alerts, recommendations, and policies. Crucially for User2's tasks, it also allows them to dismiss alerts and apply security recommendations (like enabling encryption or a specific configuration on a resource). It does not allow them to edit policies or change global settings, aligning perfectly with the principle of least privilege.
Incorrect Option:
Owner:
This role has full administrative access to all resources in the subscription, including the ability to manage role assignments. This is excessive privilege for both users' defined tasks.
Contributor:
This role can create and manage all types of Azure resources but cannot grant access to others. While a Contributor could perform some of the tasks, it grants broad permissions far beyond what is needed (e.g., creating VMs, storage accounts) and does not specifically include the ability to assign policy initiatives, which is a management plane permission more aligned with the Security Administrator role.
(For User2) Security administrator:
This role would grant User2 unnecessary permissions to edit security policies and enable provisioning, violating the least privilege principle.
Reference:
Microsoft Learn, "Azure built-in roles" documentation for Security Administrator and Security Reader. The Security Reader role explicitly includes permissions to "view security policies, states, and recommendations" and to "dismiss alerts."
| Page 2 out of 16 Pages |