Topic 3: Mix Questions
Your on-premises network contains an e-commerce web app that was developed in Angular and Nodejs. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
A. Yes
B. No
Explanation: When using Azure-provided PaaS services (e.g., Azure Storage, Azure Cosmos DB, or Azure Web App, use the PrivateLink connectivity option to ensure all data exchanges are over the private IP space and the traffic never leaves the Microsoft network.
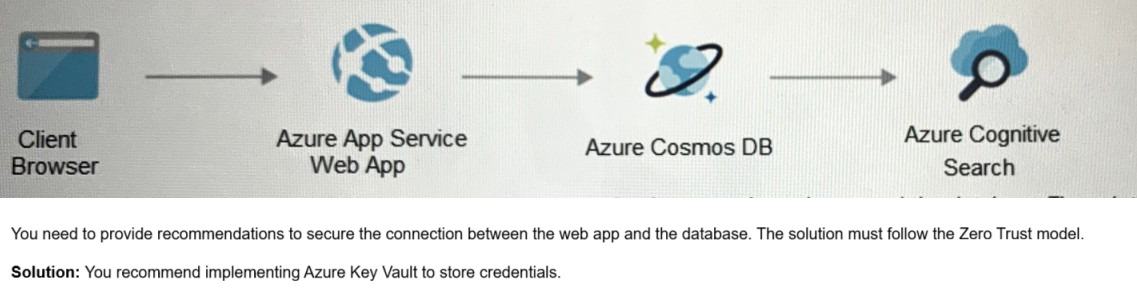
Your company has an on-premises network and an Azure subscription.
The company does NOT have a Site-to-Site VPN or an ExpressRoute connection to Azure.
You are designing the security standards for Azure App Service web apps. The web apps
will access Microsoft SQL Server databases on the network.
You need to recommend security standards that will allow the web apps to access the
databases. The solution must minimize the number of open internet-accessible endpoints
to the on-premises network.
What should you include in the recommendation?
A. a private endpoint
B. hybrid connections
C. virtual network NAT gateway integration
D. virtual network integration
Explanation: https://docs.microsoft.com/en-us/azure/app-service/app-service-hybridconnections
You have an on-premises network that has several legacy applications. The applications
perform LDAP queries against an existing directory service. You are migrating the onpremises
infrastructure to a cloud-only infrastructure.
You need to recommend an identity solution for the infrastructure that supports the legacy
applications. The solution must minimize the administrative effort to maintain the
infrastructure.
Which identity service should you include in the recommendation?
A. Azure Active Directory Domain Services (Azure AD DS)
B. Azure Active Directory (Azure AD) B2C
C. Azure Active Directory (Azure AD)
D. Active Directory Domain Services (AD DS)
Explanation: https://docs.microsoft.com/en-us/azure/active-directory-domainservices/ overview
A customer follows the Zero Trust model and explicitly verifies each attempt to access its
corporate applications.
The customer discovers that several endpoints are infected with malware.
The customer suspends access attempts from the infected endpoints.
The malware is removed from the end point.
Which two conditions must be met before endpoint users can access the corporate
applications again? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Microsoft Defender for Endpoint reports the endpoints as compliant.
B. Microsoft Intune reports the endpoints as compliant.
C. A new Azure Active Directory (Azure AD) Conditional Access policy is enforced.
D. The client access tokens are refreshed.
D. The client access tokens are refreshed.
Explanation:
https://www.microsoft.com/security/blog/2022/02/17/4-best-practices-toimplement-
a-comprehensive-zero-trust-security-approach/
https://docs.microsoft.com/en-us/azure/active-directory/develop/refresh-tokens
Your company is developing an invoicing application that will use Azure Active Directory (Azure AD) B2C. The application will be deployed as an App Service web app. You need to recommend a solution to the application development team to secure the application from identity related attacks. Which two configurations should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD Conditional Access integration with user flows and custom policies
B. Azure AD workbooks to monitor risk detections
C. custom resource owner password credentials (ROPC) flows in Azure AD B2C
D. access packages in Identity Governance
E. smart account lockout in Azure AD B2C
E. smart account lockout in Azure AD B2C
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/threatmanagement
https://docs.microsoft.com/en-us/azure/active-directory-b2c/conditional-access-userflow?
pivots=b2c-user-flow
You use Azure Pipelines with Azure Repos to implement continuous integration and continuous deployment (O/CD) workflows for the deployment of applications to Azure. You need to recommend what to include in dynamic application security testing (DAST) based on the principles of the Microsoft Cloud Adoption Framework for Azure. What should you recommend?
A. unit testing
B. penetration testing
C. dependency testing
D. threat modeling
You are designing a security strategy for providing access to Azure App Service web apps
through an Azure Front Door instance. You need to recommend a solution to ensure that
the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions based on HTTP headers that have the Front
Door ID.
Does this meet the goal?
A. Yes
B. No
Explanation: https://docs.microsoft.com/en-us/azure/frontdoor/front-door-faq#how-do-ilock- down-the-access-to-my-backend-to-only-azure-front-door-
You have an Azure subscription that contains a Microsoft Sentinel workspace.
Your on-premises network contains firewalls that support forwarding event logs m the
Common Event Format (CEF). There is no built-in Microsoft Sentinel connector for the
firewalls.
You need to recommend a solution to ingest events from the firewalls into Microsoft
Sentinel.
What should you include m the recommendation?
A. an Azure logic app
B. an on-premises Syslog server
C. an on-premises data gateway
D. Azure Data Factory
Azure subscription that uses Azure Storage.
The company plans to share specific blobs with vendors. You need to recommend a
solution to provide the vendors with secure access to specific blobs without exposing the
blobs publicly. The access must be t\me-Vim\ted. What should you include in the
recommendation?
A. Create shared access signatures (SAS).
B. Share the connection string of the access key.
C. Configure private link connections.
D. Configure encryption by using customer-managed keys (CMKs)
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. app discovery anomaly detection policies in Microsoft Defender for Cloud Apps
B. adaptive application controls in Defender for Cloud
C. Azure Security Benchmark compliance controls m Defender for Cloud
D. app protection policies in Microsoft Endpoint Manager
Explanation: https://docs.microsoft.com/en-us/azure/defender-forcloud/ recommendations-reference#compute-recommendations
| Page 5 out of 18 Pages |