Topic 3: Mix Questions
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result,
these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8
points.
You need to recommend configurations to increase the score of the Secure management
ports controls.
Solution: You recommend enabling the VMAccess extension on all virtual machines.
Does this meet the goal?
A. Yes
B. No
Explanation:
https://docs.microsoft.com/en-us/security/benchmark/azure/security-controlsv3-
privileged-access#pa-2-avoid-standing-access-for-user-accounts-and-permissions
Adaptive Network Hardening:
https://docs.microsoft.com/enus/
security/benchmark/azure/security-controls-v3-network-security#ns-7-simplify-networksecurity-
configuration
You have Microsoft Defender for Cloud assigned to Azure management groups.
You have a Microsoft Sentinel deployment.
During the triage of alerts, you require additional information about the security events,
including suggestions for remediation. Which two components can you use to achieve the
goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. workload protections in Defender for Cloud
B. threat intelligence reports in Defender for Cloud
C. Microsoft Sentinel notebooks
D. Microsoft Sentinel threat intelligence workbooks
D. Microsoft Sentinel threat intelligence workbooks
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/understand-threatintelligence
https://docs.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloudintroduction
https://docs.microsoft.com/en-us/azure/defender-for-cloud/threat-intelligencereports
https://docs.microsoft.com/en-us/azure/sentinel/notebooks
Your company has a hybrid cloud infrastructure.
The company plans to hire several temporary employees within a brief period. The
temporary employees will need to access applications and data on the company' premises
network.
The company's security policy prevents the use of personal devices for accessing company
data and applications.
You need to recommend a solution to provide the temporary employee with access to
company resources. The solution must be able to scale on demand.
What should you include in the recommendation?
A. Migrate the on-premises applications to cloud-based applications.
B. Redesign the VPN infrastructure by adopting a split tunnel configuration.
C. Deploy Microsoft Endpoint Manager and Azure Active Directory (Azure AD) Conditional Access.
D. Deploy Azure Virtual Desktop, Azure Active Directory (Azure AD) Conditional Access, and Microsoft Defender for Cloud Apps.
Explanation:
https://docs.microsoft.com/en-us/azure/architecture/examplescenario/
wvd/windows-virtual-desktop
https://docs.microsoft.com/en-us/azure/virtual-desktop/security-guide
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/announcingmicrosoft-
defender-for-cloud-apps/ba-p/2835842
You are designing a security strategy for providing access to Azure App Service web apps
through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through
the Front Door instance.
Solution: You recommend access restrictions that allow traffic from the Front Door service
tags.
Does this meet the goal?
A. Yes
B. No
Explanation: https://docs.microsoft.com/en-us/azure/app-service/app-service-iprestrictions# restrict-access-to-a-specific-azure-front-door-instance
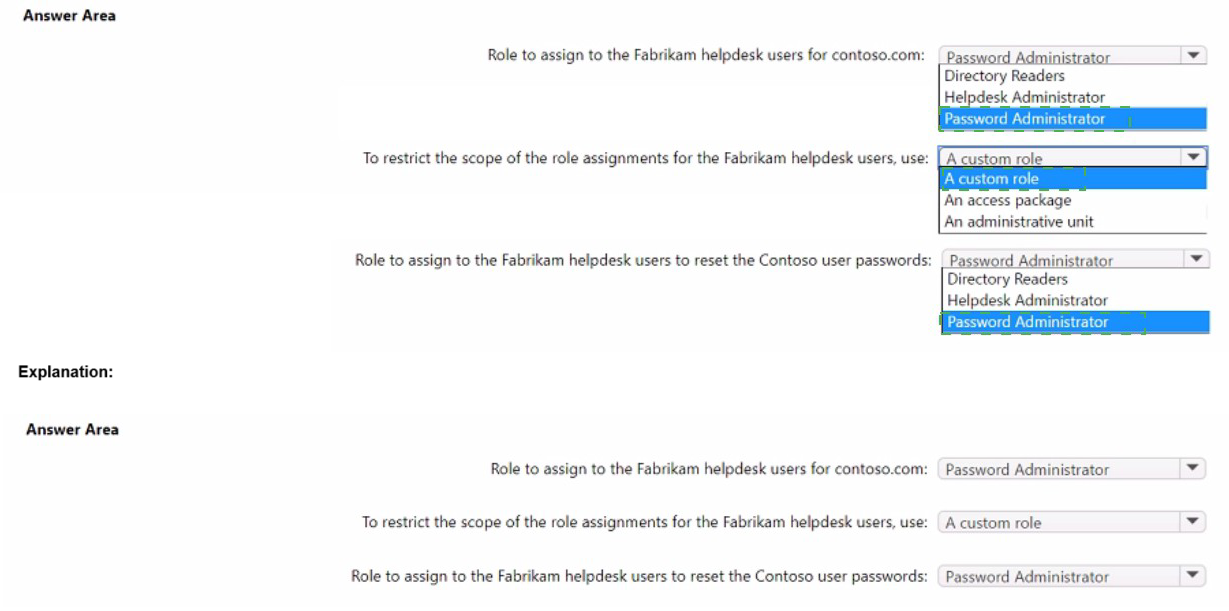
Your company, named Contoso. Ltd... has an Azure AD tenant namedcontoso.com.
Contoso has a partner company named Fabrikam. Inc. that has an Azure AD tenant named
fabrikam.com. You need to ensure that helpdesk users at Fabrikam can reset passwords
for specific users at Contoso. The solution must meet the following requirements:
• Follow the principle of least privilege.
• Minimize administrative effort.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

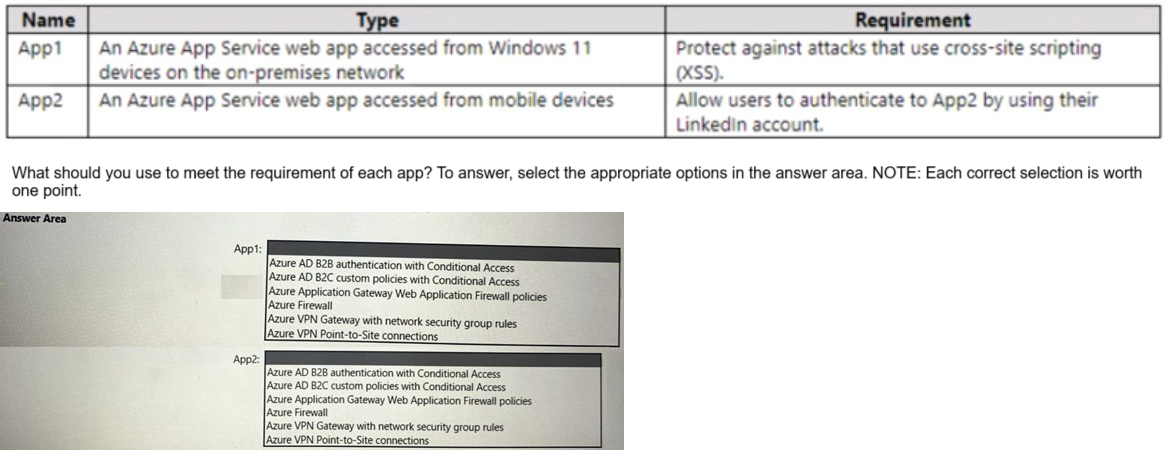
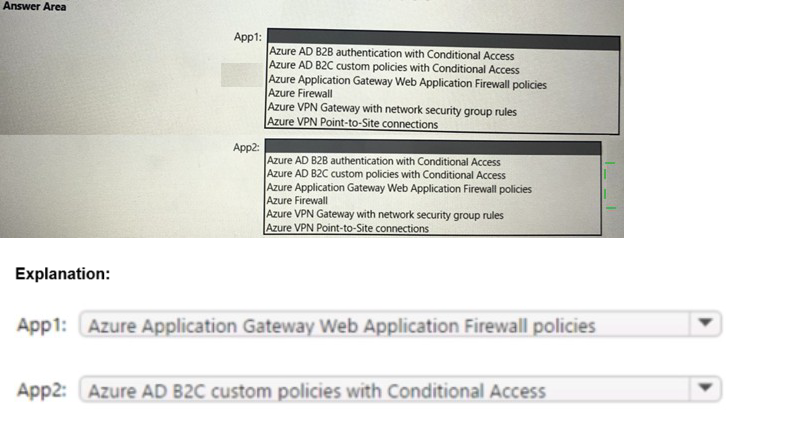
You have a hybrid cloud infrastructure.
You plan to deploy the Azure applications shown in the following table.
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud.
You receive the following recommendations in Defender for Cloud.
• Access to storage accounts with firewall and virtual network configurations should be
restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the
recommendations. What should you recommend?
A. Azure Storage Analytics
B. Azure Network Watcher
C. Microsoft Sentinel
D. Azure Policy
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/security-policyconcept
https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/storagesecurity-
baseline
You have a Microsoft 365 subscription.
You are designing a user access solution that follows the Zero Trust principles of the
Microsoft Cybersecurity Reference Architectures (MCRA).
You need to recommend a solution that automatically restricts access to Microsoft
Exchange Online. SharePoint Online, and Teams m near-real-lime (NRT) in response to
the following Azure AD events:
• A user account is disabled or deleted
• The password of a user is changed or reset.
• All the refresh tokens for a user are revoked
• Multi-factor authentication (MFA) is enabled for a user
Which two features should you include in the recommendation? Each correct answer
presents part of the solution. NOTE: Each correct selection is worth one point.
A. continuous access evaluation
B. a sign-in risk policy
C. Azure AD Privileged Identity Management (PIM)
D. Conditional Access
E. Azure AD Application Proxy
D. Conditional Access
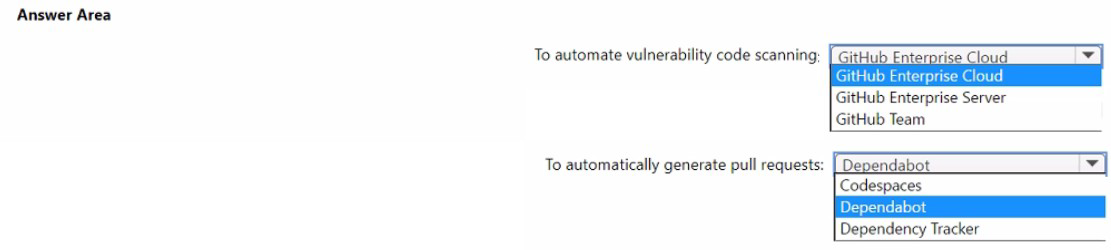
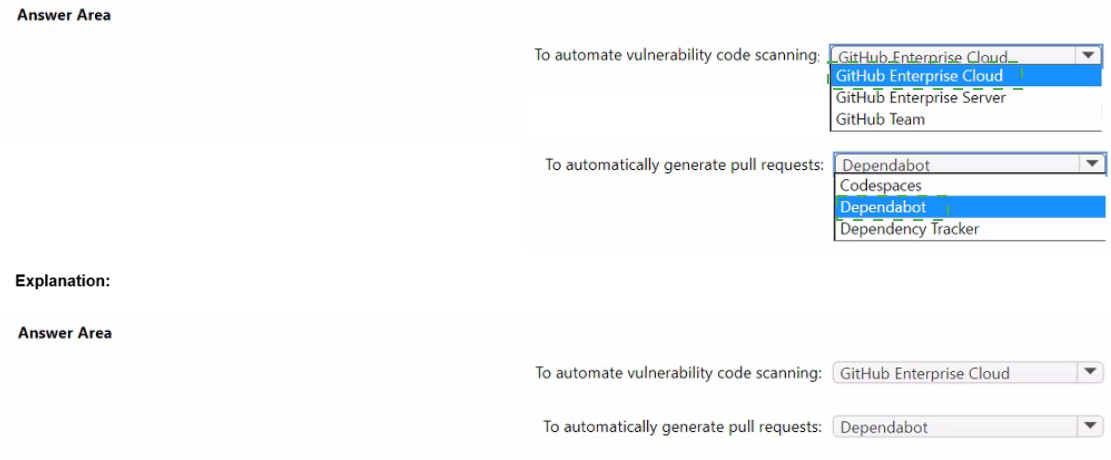
You plan to automate the development and deployment of a Nodejs-based app by using
GitHub.
You need to recommend a DevSecOps solution for the app. The solution must meet the
following requirements:
• Automate the generation of pull requests that remediate identified vulnerabilities.
• Automate vulnerability code scanning for public and private repositories.
• Minimize administrative effort.
• Minimize costs.
What should you recommend using? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Your company is designing an application architecture for Azure App Service Environment (ASE) web apps as shown in the exhibit. (Click the Exhibit tab.)
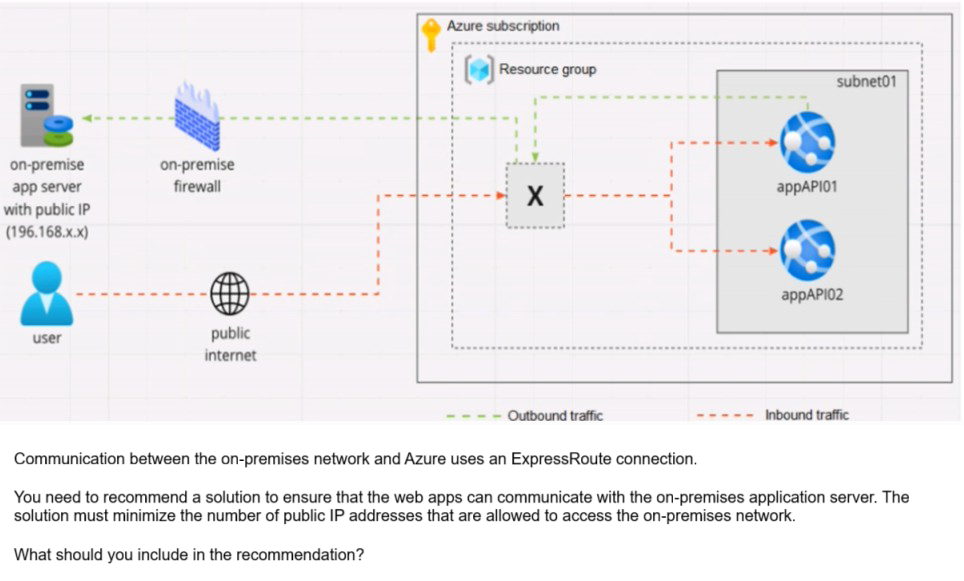
A. Azure Traffic Manager with priority traffic-routing methods
B. Azure Application Gateway v2 with user-defined routes (UDRs).
C. Azure Front Door with Azure Web Application Firewall (WAF)
D. Azure Firewall with policy rule sets
Explanation: https://docs.microsoft.com/en-us/azure/web-application-firewall/afds/afdsoverview
| Page 4 out of 18 Pages |