Topic 4: Mix Questions
You have an Azure subscription that contains an Azure key vault named ContosoKey1.
You create users and assign them roles as shown in the following table.
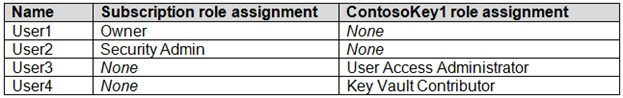
You need to identify which users can perform the following actions:
Delegate permissions for ContsosKey1.
Configure network access to ContosoKey1.
Which users should you identify? To answer, select the appropriate options in the answer
area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription named Subscription1 that contains the resources shown in
the following table.
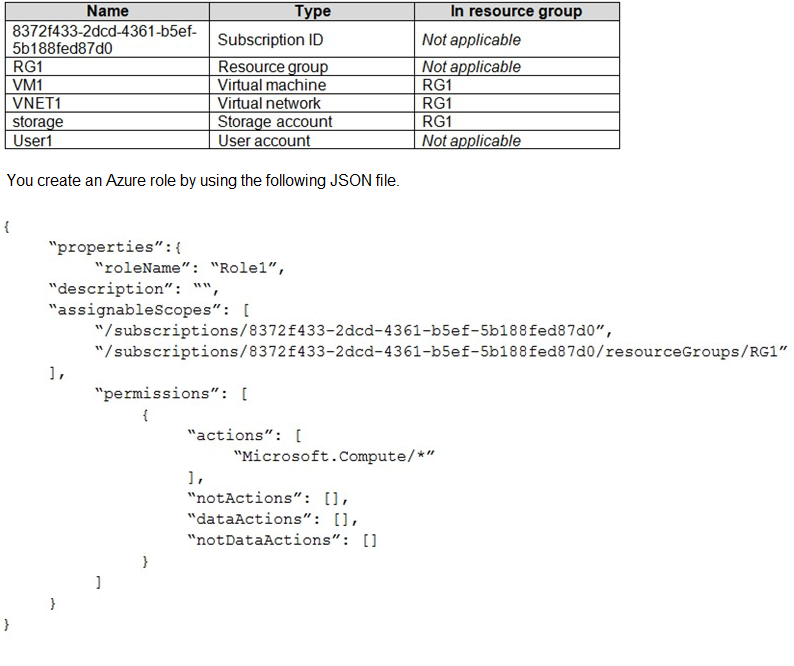
You assign Role1 to User1 for RG1.
For each of the following statements, select Yes if the statement is true. Otherwise, select
No.
NOTE: Each correct selection is worth one point.


ION NO: 180 HOTSPOT
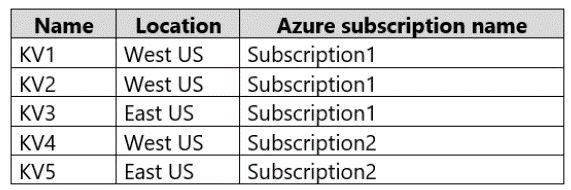
You have the Azure key vaults shown in the following table.
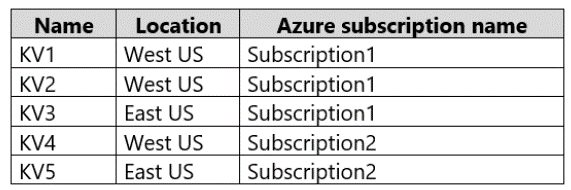
KV1 stores a secret named Secret1 and a key for a managed storage account named
Key1.
You back up Secret1 and Key1.
To which key vaults can you restore each backup? To answer, select the appropriate
options in the answer area.
NOTE: Each correct selection is worth one point.

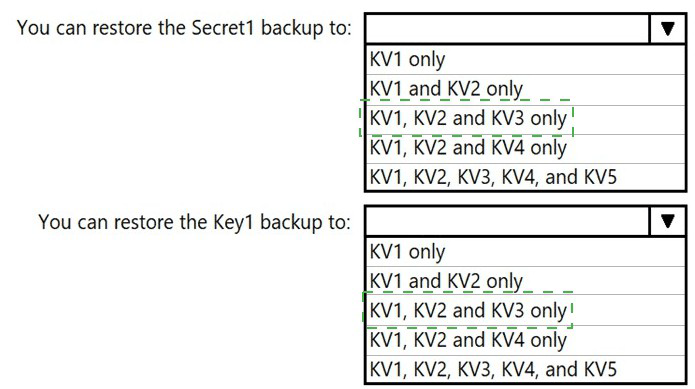
You have an Azure Storage account that contains a blob container named container! and a
client application named App1. You need to enable App1 access to container1 by using
Microsoft Entra authentication. What should you do? lo answer, select the appropriate
options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a user named Admin1 and a resource group
named RG1.
In Azure Monitor, you create the alert rules shown in the following table.
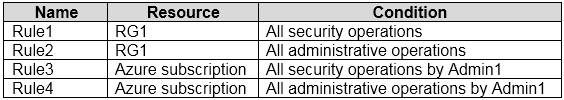
Admin1 performs the following actions on RG1:
Adds a virtual network named VNET1
Adds a Delete lock named Lock1
Which rules will trigger an alert as a result of the actions of Admin1? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
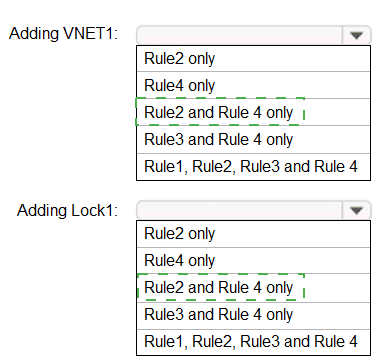
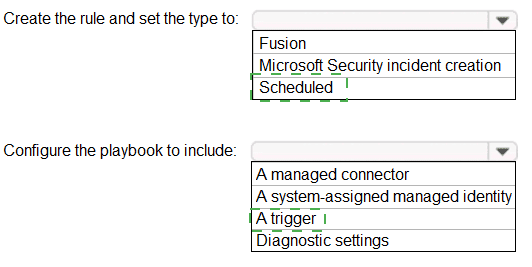
You have an Azure Sentinel workspace that contains an Azure Active Directory (Azure AD)
connector, an Azure Log Analytics query named Query1 and a playbook named
Playbook1.
Query1 returns a subset of security events generated by Azure AD.
You plan to create an Azure Sentinel analytic rule based on Query1 that will trigger
Playbook1.
You need to ensure that you can add Playbook1 to the new rule.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
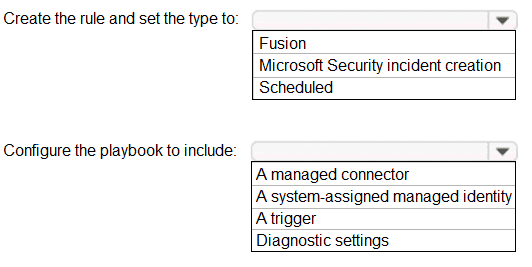
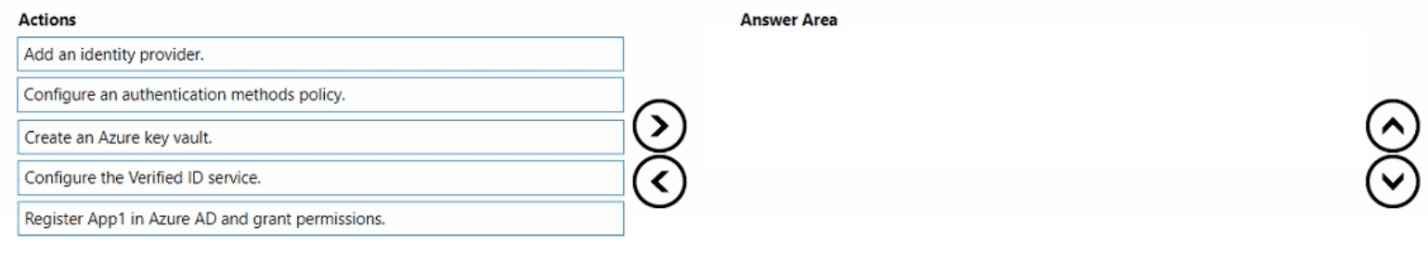
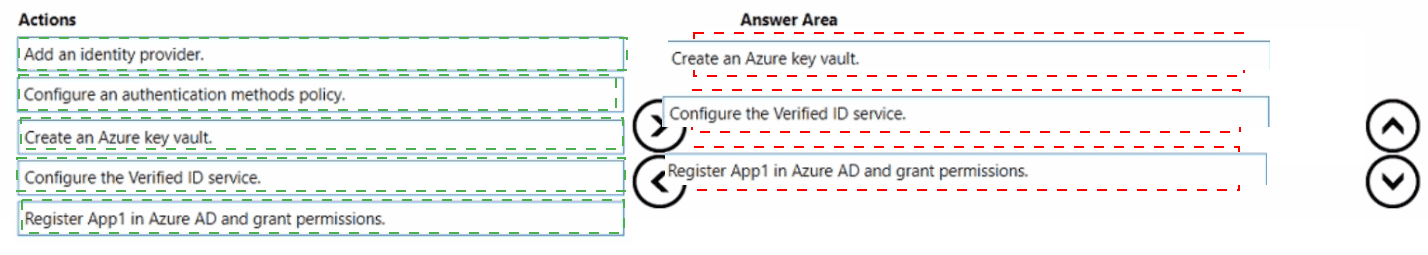
You have an Azure AD Tenant and an application named App1.
You need to ensure that App1 can use Microsoft Entra Verified ID to verify credentials.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains
the users shown in the following table.
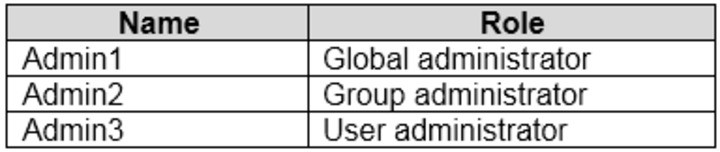
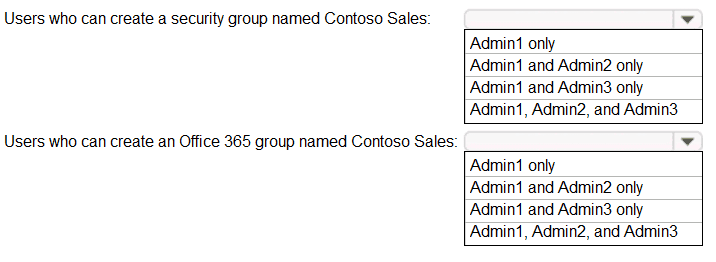
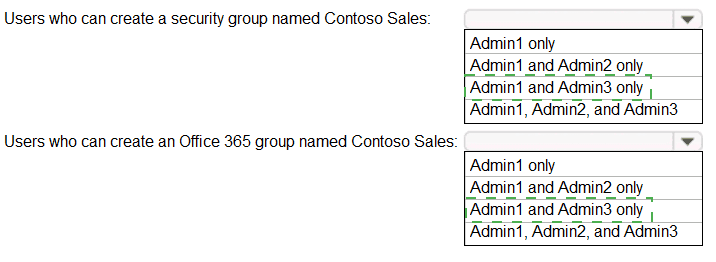
Contoso.com contains a group naming policy. The policy has a custom blocked word list rule that includes the word Contoso.
Which users can create a group named Contoso Sales in contoso.com? To answer, select
the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains the virtual machines shown in the following
table.
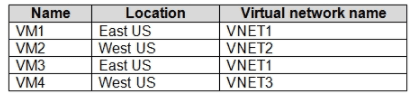
All the virtual networks are peered.
You deploy Azure Bastion to VNET2.
Which virtual machines can be protected by the bastion host?
A. VM1, VM2, VM3, and VM4
B. VM1, VM2, and VM3 only
C. VM2 and VM4 only
D. VM2 only
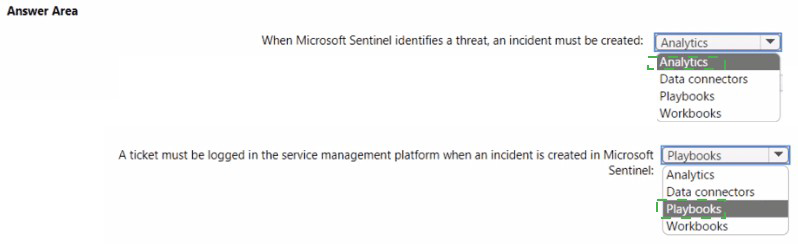
You have an Azure subscription that contains a Microsoft Sentinel workspace.
Microsoft Sentinel is configured to ingest logs from several Azure workloads. A third-party
service management platform is used to manage incidents.
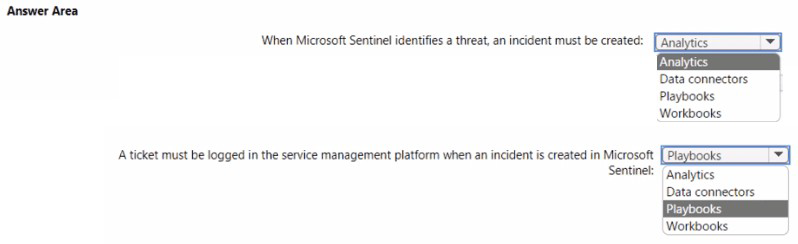
You need to identify which Microsoft Sentinel components to configure to meet the
following requirements:
• When Microsoft Sentinel identifies a threat an incident must be created.
• A ticket must be logged in the service management platform when an incident is created in Microsoft Sentinel.
Which component should you identify for each requirement? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
| Page 11 out of 50 Pages |